https://www.vulnhub.com/entry/dc-2,311/
Review
- Enumerate all ports
- Webserver is under wordpress
- Use WPscan to enumerate users
- The first flag gives a clue on using cewl to generate wordlists
- Use WPscan with the cewl wordlists to bruteforce
- Find for flag clues in the wordpress admin page
- Login to user via SSH
- Escape the restrictive shell with vi
- Switch to the next user and check for sudo permissions
- Use GTFOBins to gain root access
Enumeration
Run nmap scan to find for open ports.
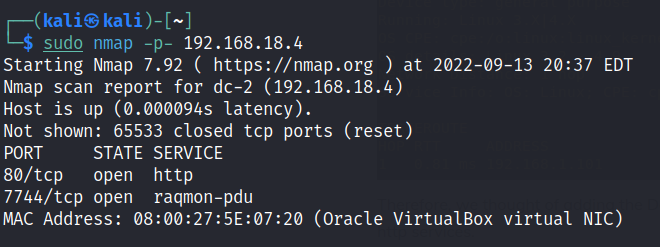

Found a clue in port 80

We need to use cewl to generate a wordlist.

Run a gobuster scan to find for hidden directories.

Since the site runs under wordpress , let’s use wpscan to enumerate.

Found 3 users.

Use cewl to generate a wordlist.
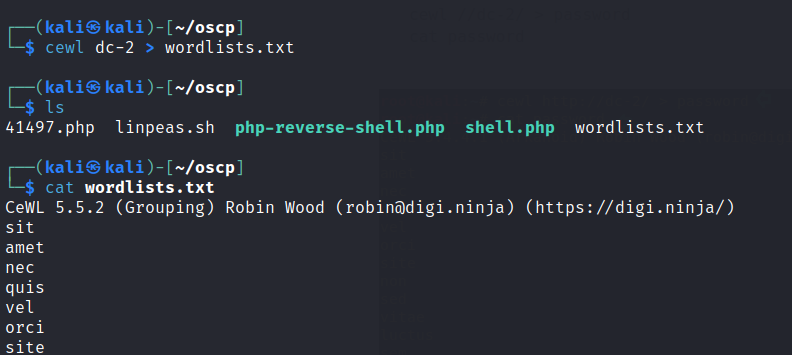
Create a user list with the users found in the scan and start another wpscan with the user list wordlists.

Found two passwords.

Foothold
jerry

Found the 2nd flag in pages.

tom user has nothing important inside.
Let’s SSH into the tom user.

We are only able to use the following commands.

We can use the following commands from GTFOBins

Then export the path to escape the restrictive shell.

We can switch user to jerry and look at sudo permissions.

Privilege escalation
Check GTFOBins for git exploits. We can use the 2nd option to gain root access.


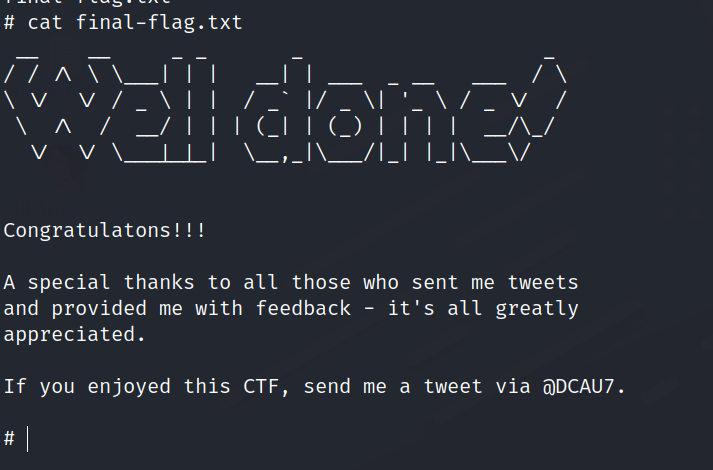
We get the final flag.