https://www.vulnhub.com/entry/photographer-1,519/
Review
- Full enumeration will show two webservers
- Port 8000 webserver runs under the Koken CMS
- Find exploit for Koken CMS on Exploit DB
- Craft a php reverse shell payload and upload the file through burpsuite request
- Edit the extension to full upload the file
- Naviagate to the payload and a revershell is gained
- Look for SUID binaries and find an exploit on GTFOBins to gain root access
Enumeration
Run nmap scan to find for open ports.



Port 80
Port 8000

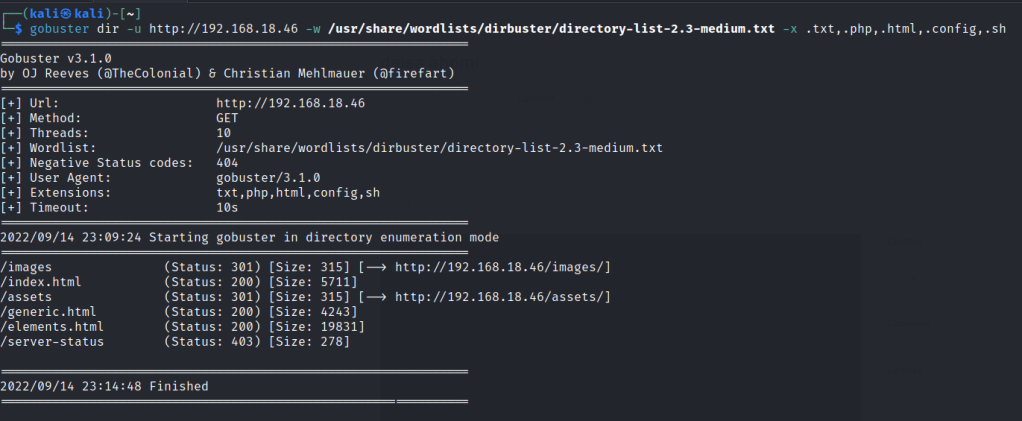
Run a gobuster scan to find for hidden directories.
SMB Enumeration


mailsent.txt

From port 8000 we can see it runs on the Koken cms.
Find the admin page.

login with the sent user email id and the password as the clue.

Foothold
Search an exploit online
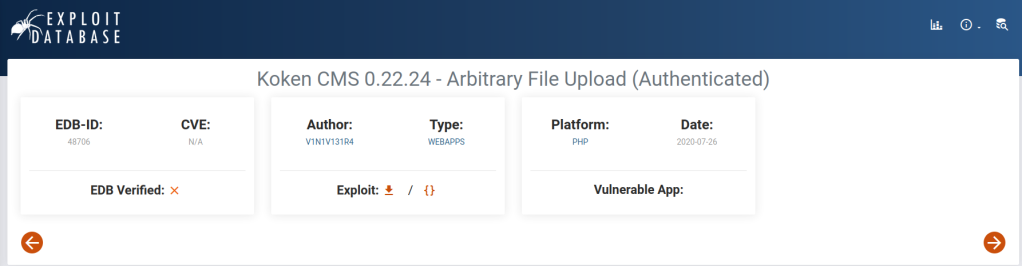

From the exploit information we need to craft a reverse shell php payload with .jpg extension and forward it to burpsuite. From there we remove the .jpg extension and forward the request.

Payload uploaded

Back to the 8000 webserver we click on the download file link of the payload.

Set up a nc listener a shell is gained.

The first flag is found.

Privilege escalation
Search for setuid binaries and we can use the php7.2 binary.

Use GTFOBins to get a php SUID exploit

Root access is gained.
