https://www.vulnhub.com/entry/inclusiveness-1,422/
Review
- Driectory enumeration indicates robots.txt can be seen with a regular user-agent
- Use curl to bypass the user-agent with Googlebot to find a clue
- Hidden directory can be exploited by LFI
- Test out the LFI exploit by uploading a PHP webshell
- Create a PHP reverse shell and upload to get a shell
- Explore system to find a rootshell program
- Edit configuration to gain root access
Enumeration
Run nmap scan to find for open ports.
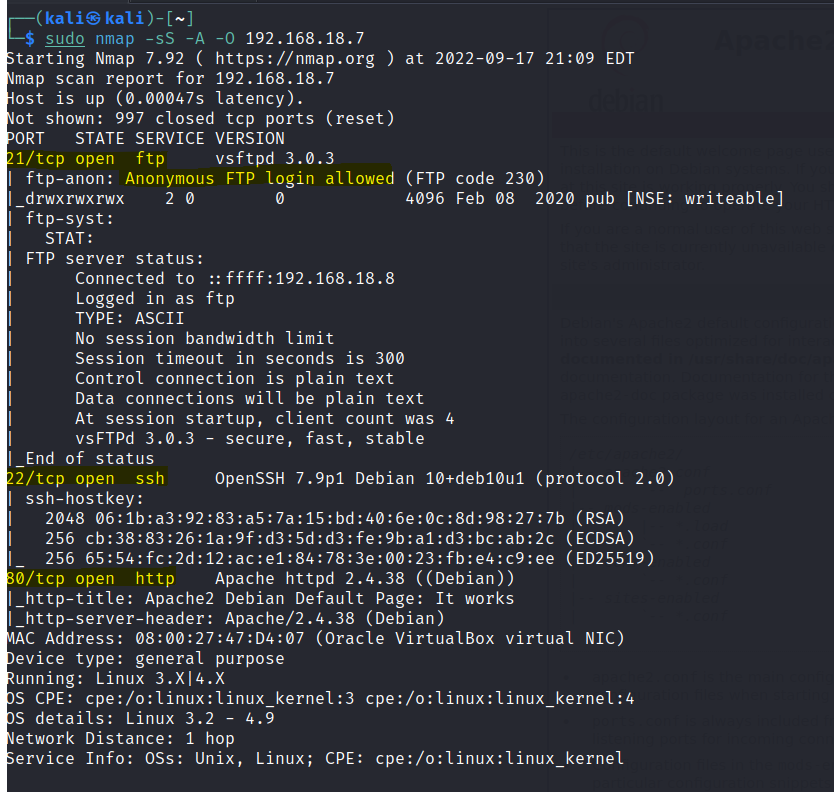
Run a gobuster scan to find for hidden directories.
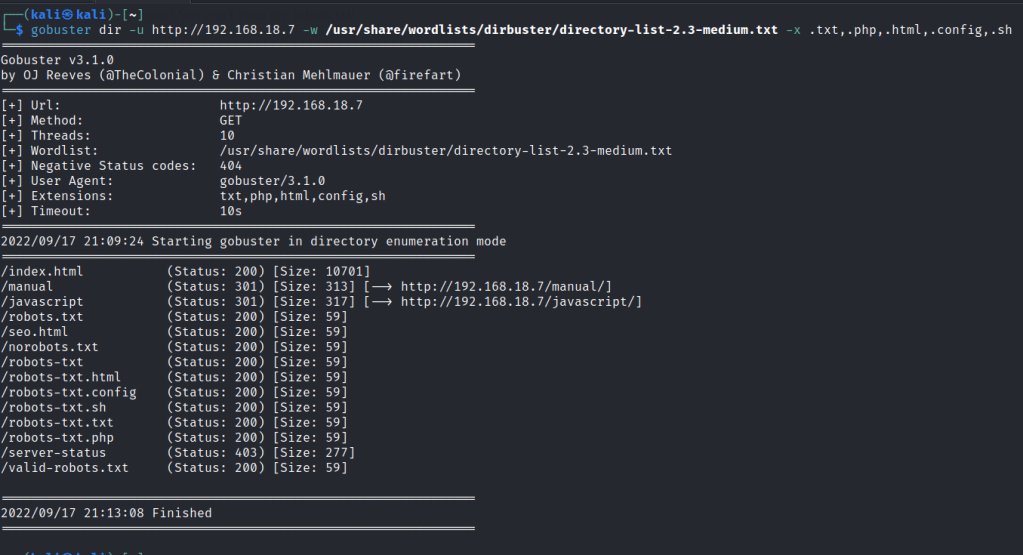
Most of the robots pages shows this.
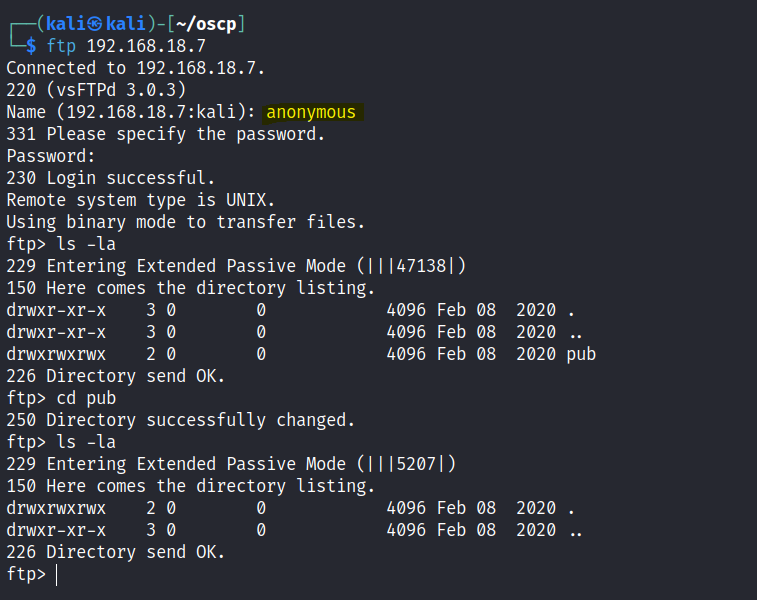
FTP
Lets’ bypass the useragent with google bot in curl

/secret_information/
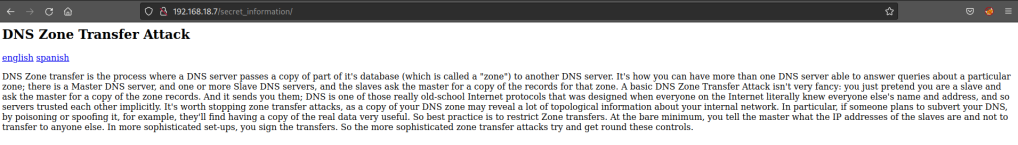
Tried to do some DNS enumeration but there wasn’t much. However upon noticing the URL of the secret information, I decided to try a directory reversal.

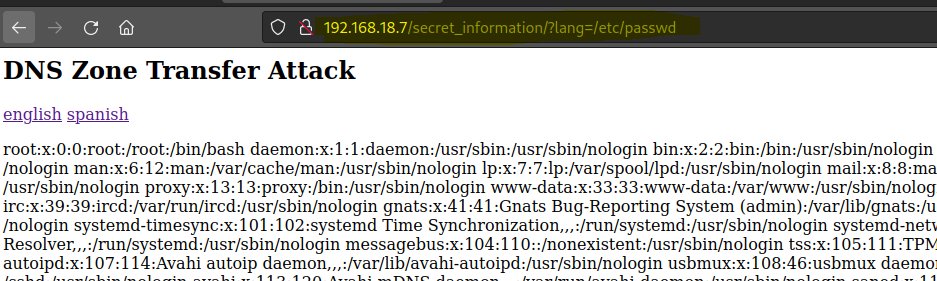
Since we know the FTP runs vsftpd, let’s search for a config file.
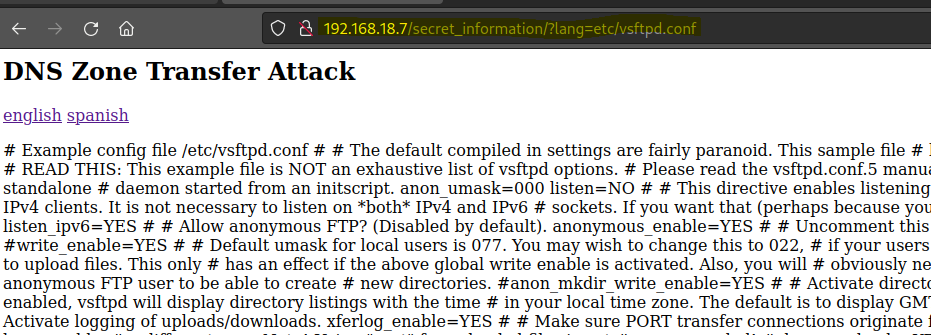

Create a PHP webshell.


Upload it into the FTP server.

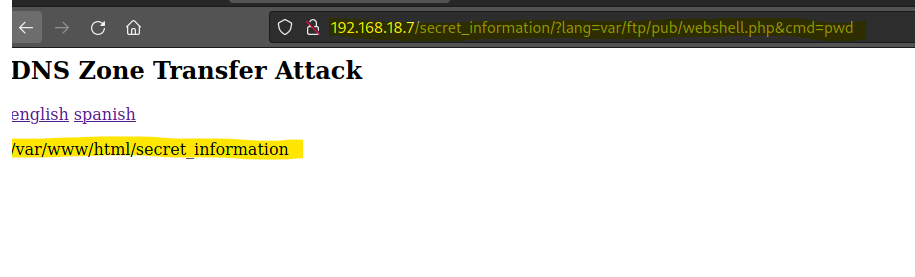
Let’s test the webshell
Now let’s enter a PHP reverse shell payload.
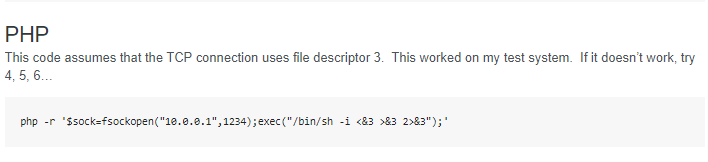
Encode the one liner PHP reverse shell.

Paste the encoded script into the webshell, start a netcat listener and a shell is gained.

Foothold

Checking Tom directory we find a rootshell.c

Privilege escalation
Head to the tmp directory and create a whoami file with tom. Then export the path.

Run the rootshell again and root access is gained.
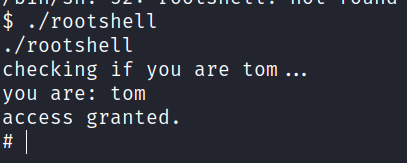
Final flag found.
