Windows Reversing
https://www.malwaretech.com/challenges/windows-reversing
Static Analysis
Strings1
strings1.exe contains an un-encrypted flag stored within the executable. When run, the program will output an MD5 hash of the flag but not the original. Can you extract the flag?
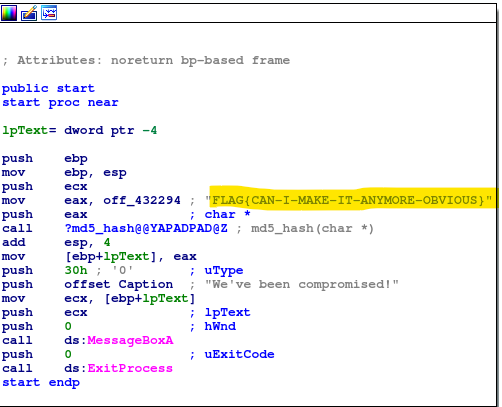
Strings2
strings2.exe contains an un-encrypted flag stored within the executable. When run, the program will output an MD5 hash of the flag but not the original. Can you extract the flag?

Use a hex to string converter to get the flag.

Strings3
strings3.exe contains an un-encrypted flag stored within the executable. When run, the program will output an MD5 hash of the flag but not the original. Can you extract the flag?
Analyze the file in Ghidra. From the decompiler we can see that the function LoadString loads a string with the arguments beside.


There is a Rsrc string table that is numbered.
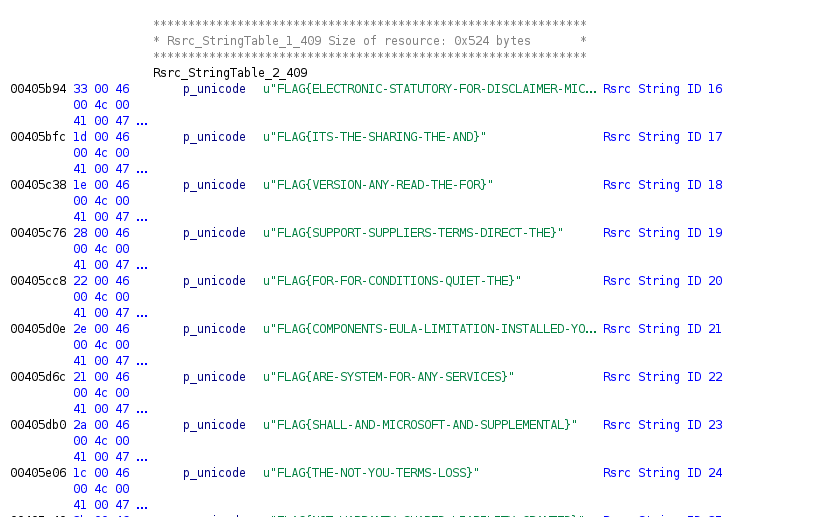
Hex 0x110 = Decimal 272
Flag is found
