https://app.letsdefend.io/challenge/port-scan-activity/

First download the Log file which contains a pcap file and open it in Wireshark.
Question 1
What is the IP address scanning the environment?
We can see that is 10.42.42.253 sending a TCP 3-way handshake to a couple of different IP addresses. This suggests that that particular IP address is initiating a scan.

Answer: 10.42.42.253
Question 2
What is the IP address found as a result of the scan?
Sort the protocol and look for NBNS.

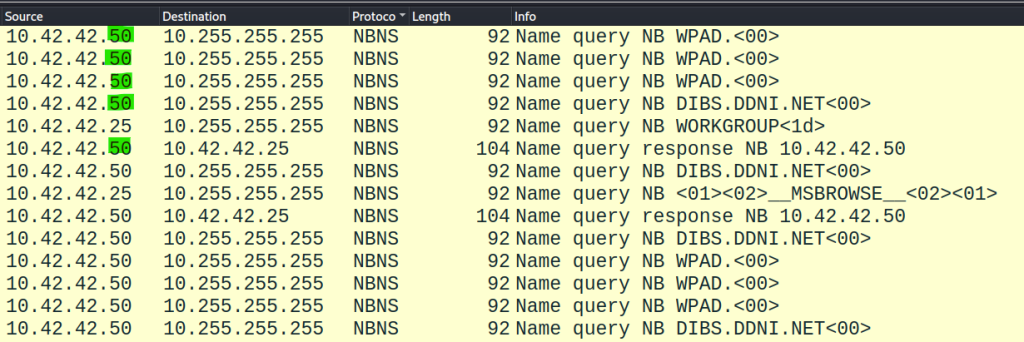
10.42.42.50 is the only IP address that responds back to the name query.
Answer: 10.42.42.50
Question 3
What is the MAC address of the Apple system it finds?
Head to Statistics –> Conversations –> Ethernet tab and toggle the Name Resolution option at the bottom. We are able to find a Apple system.

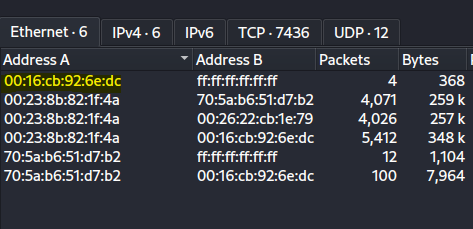
Answer: 00:16:cb:92:6e:dc
Question 4
What is the IP address of the detected Windows system?
Head to Statistics –> Endpoint –> IPv4
From what we gather so far:
- 10.42.42.25 – Apple System
- 10.42.42.50 – Windows System
- 10.42.42.56 – Unknown System
- 10.42.42.253 – Attacking System
- 10.255.255.255 – Network Broadcast Address
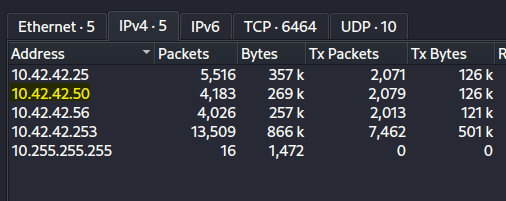
Answer: 10.42.42.50