https://app.letsdefend.io/training/lesson_detail/dynamic-malware-analysis-example-1
Connect to the Hands-On Practice lab in the page. LetsDefend has set up a system with the necessary tools for the malware analysis.

Since it is dynamic analysis we should set up the following tools before running the malware.
Start up Process Hacker which is a free, powerful, multi-purpose tool that helps you monitor system resources, debug software and detect malware
Then Process Monitor, which is an advanced monitoring tool for Windows that shows real-time file system, Registry and process/thread activity
Net will be WireShark which is a widely-used network protocol analyzer.

Lastly it will be Fiddler that helps you debug web applications by capturing network traffic between the Internet and test computers.
Unzip the malware and execute the file.
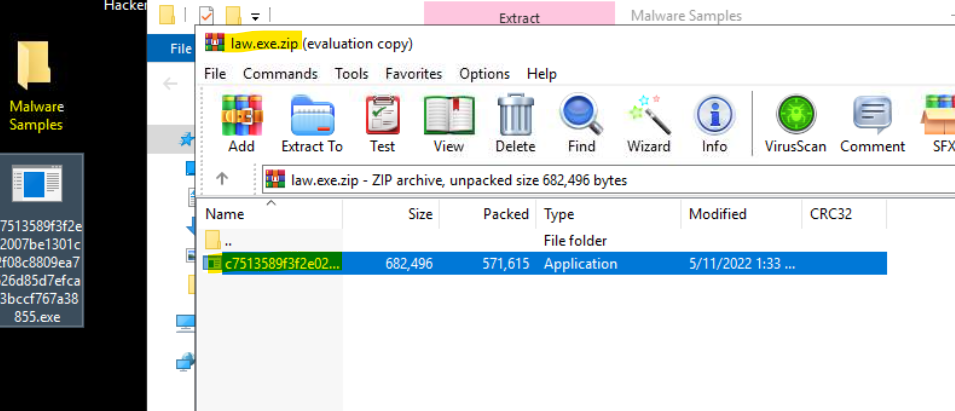
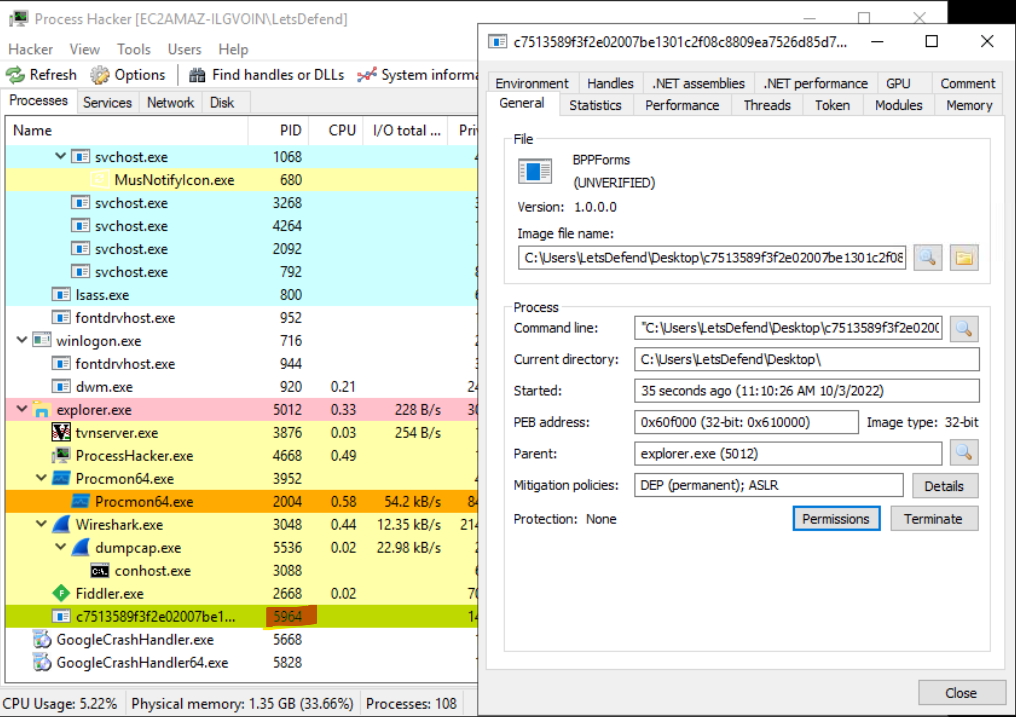
Head to process hacker and check if the malware is running. Take note of the process ID (PID).
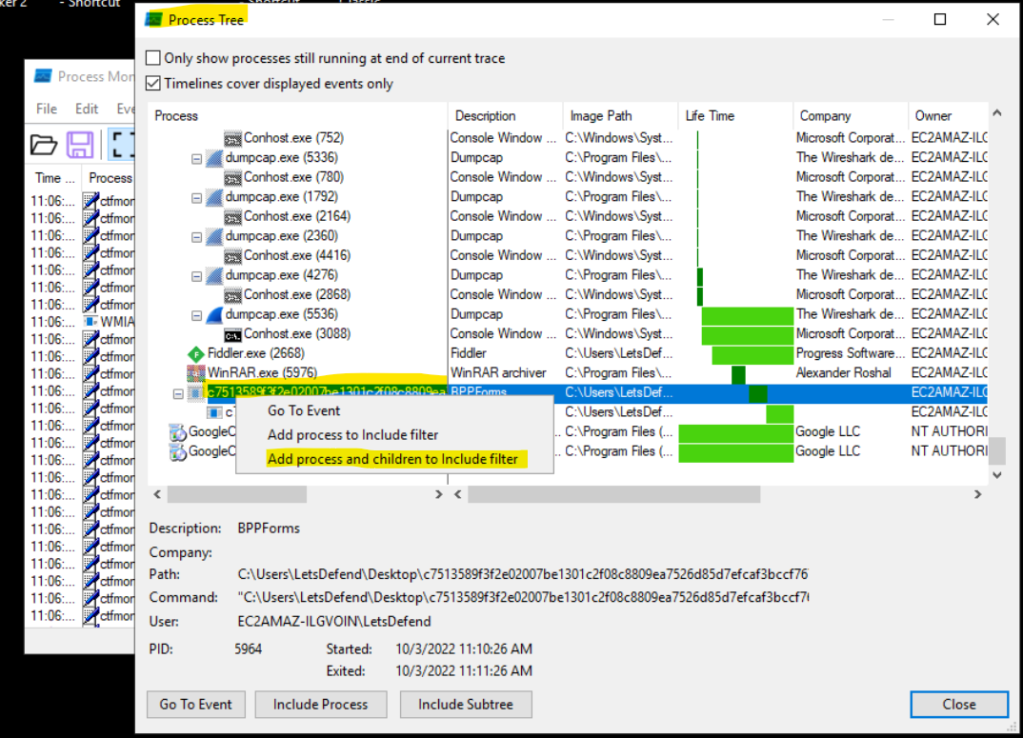
Head to process monitor, use the process tree function to have a better view of the processes running. Search for the malware and add process and children to include filer.
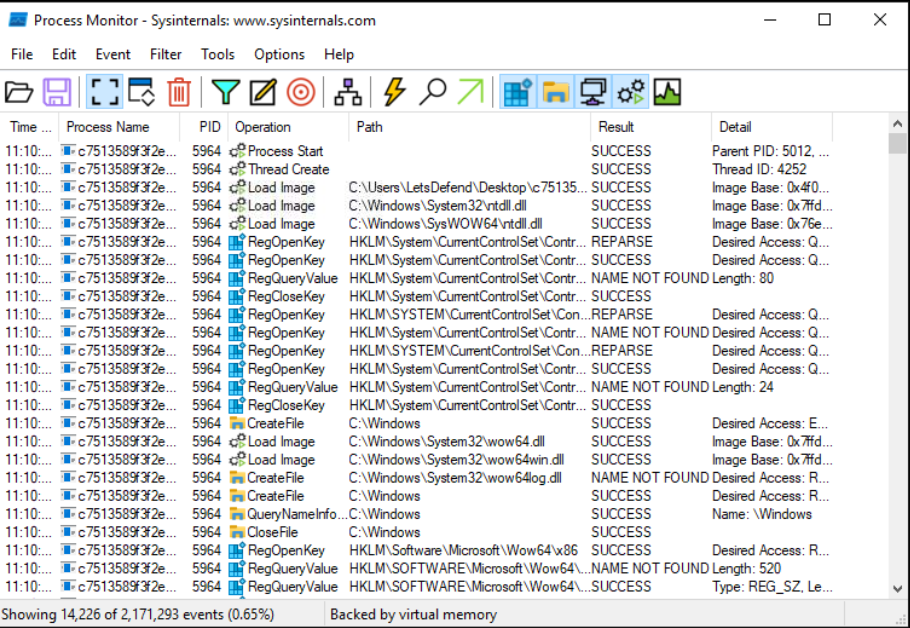
Now we can only see the process that the malware executes.
We can check the network connection in fiddler too.
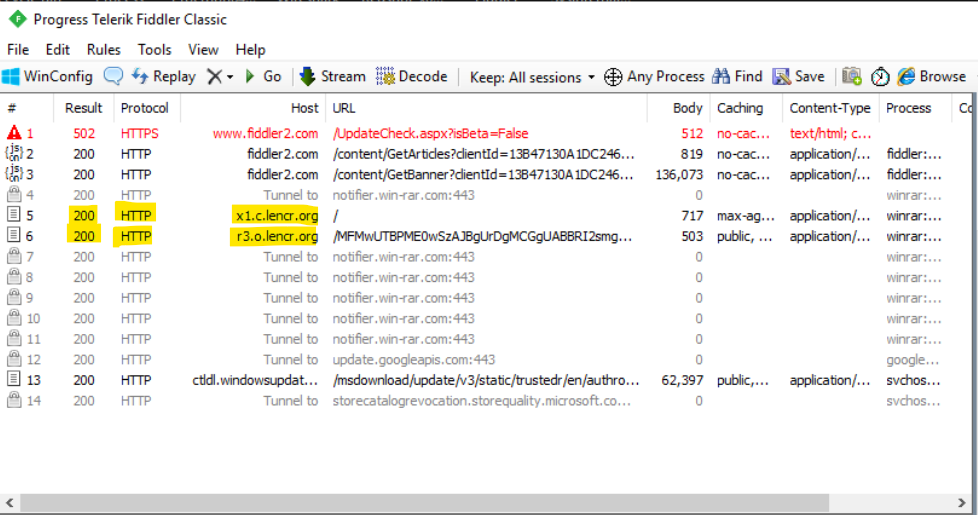
Question 1
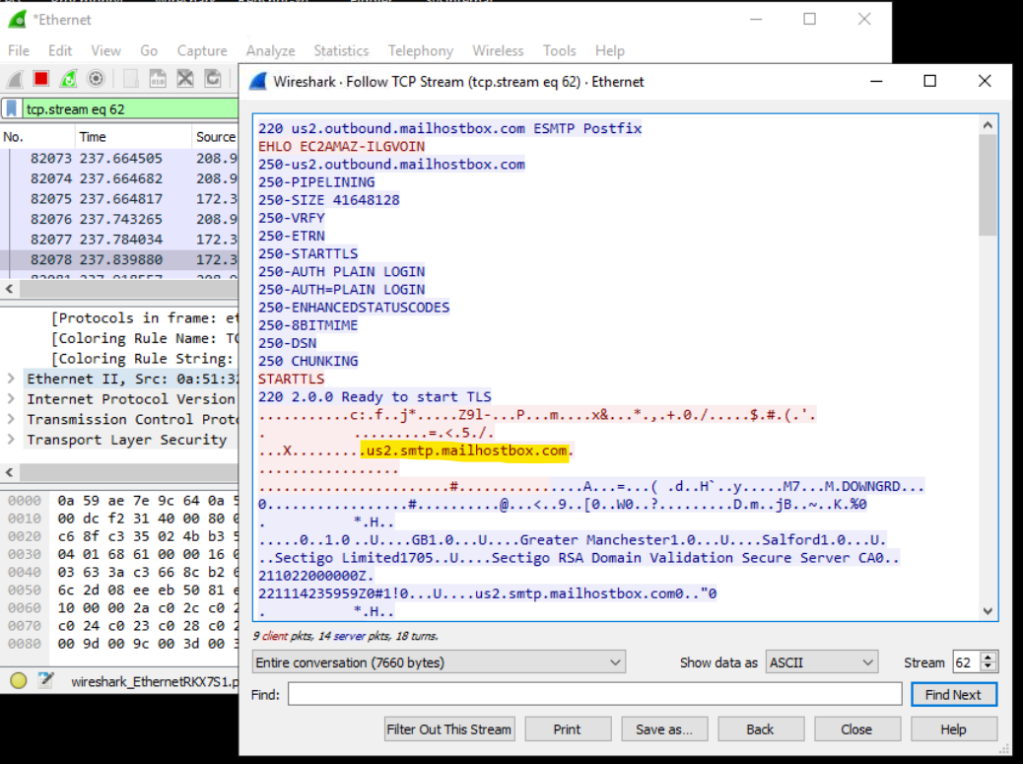
What is the domain name that the malware connects to for data hijacking?
Head to WireShark and filter to SMTP then follow the stream to see the connections. We can see a domain name in the TCP stream.
Question 2
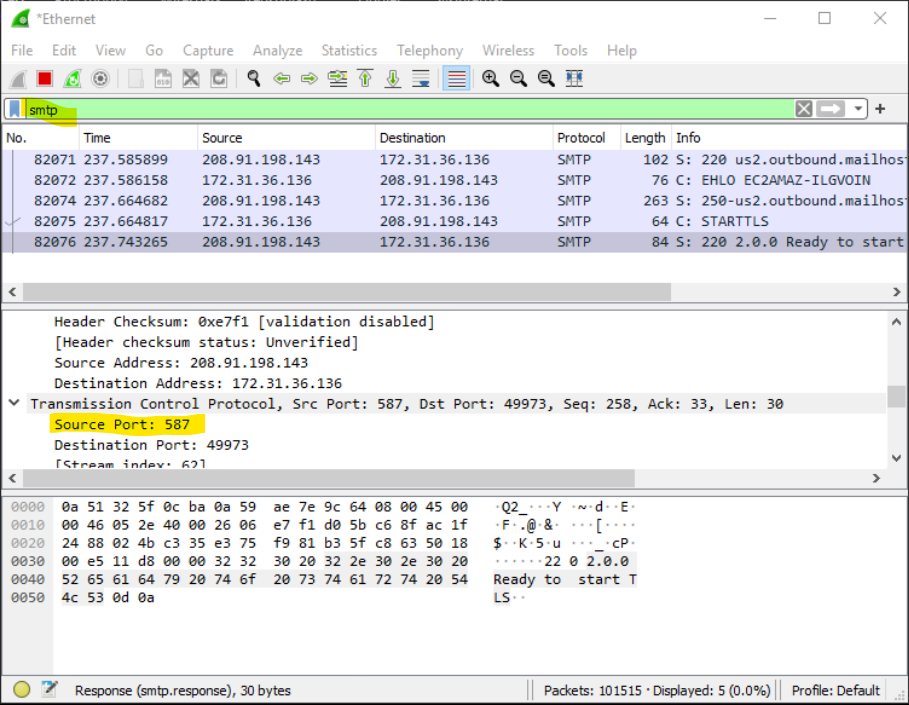
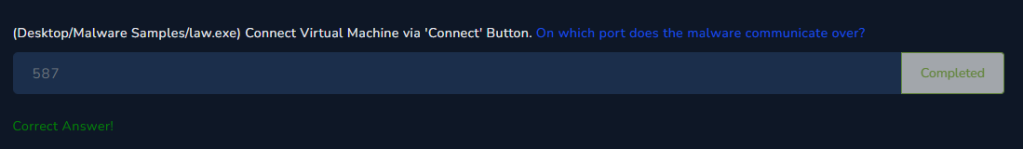
On which port does the malware communicate over?
SMTP runs on port 587
Question 3
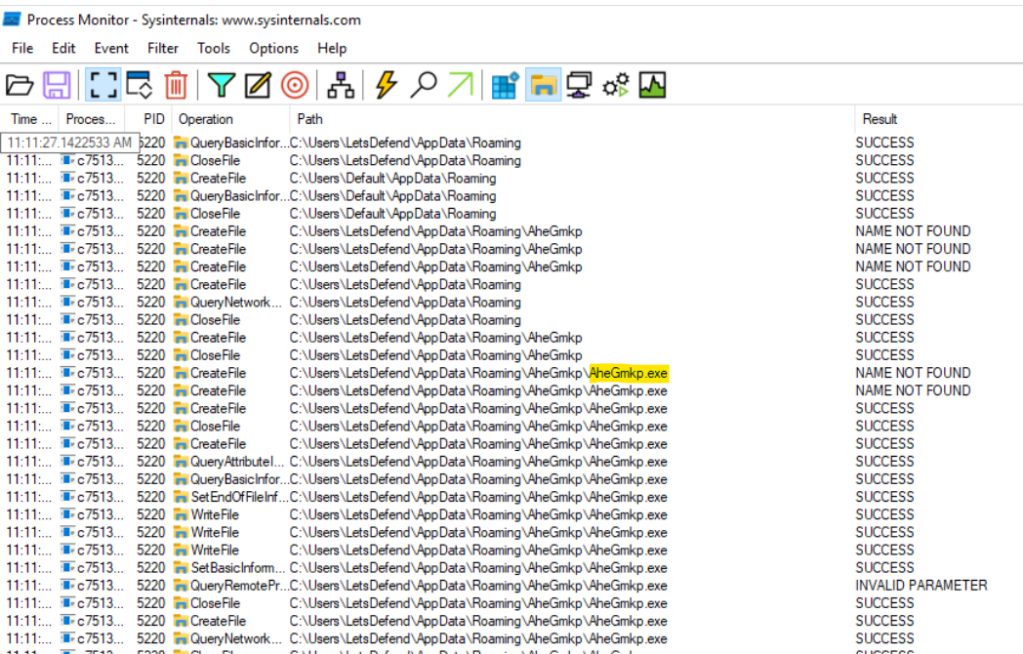
What is the name of the executable file that the malicious application writes to the AppData directory?
Since there are many processes we can just filter the processes. We can add a filter rule to only look at the paths that contains AppData. We can then see an executable.

Question 4
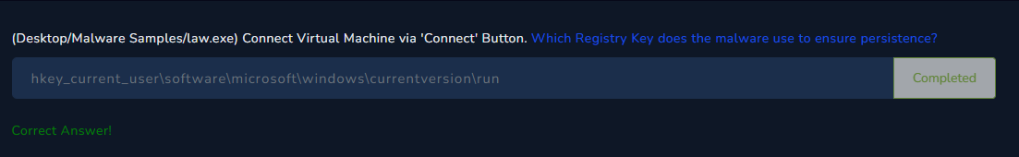
Which Registry Key does the malware use to ensure persistence?
We can check for common Registry Key that ensures persistence. The lessons before hand had introduced some for us.
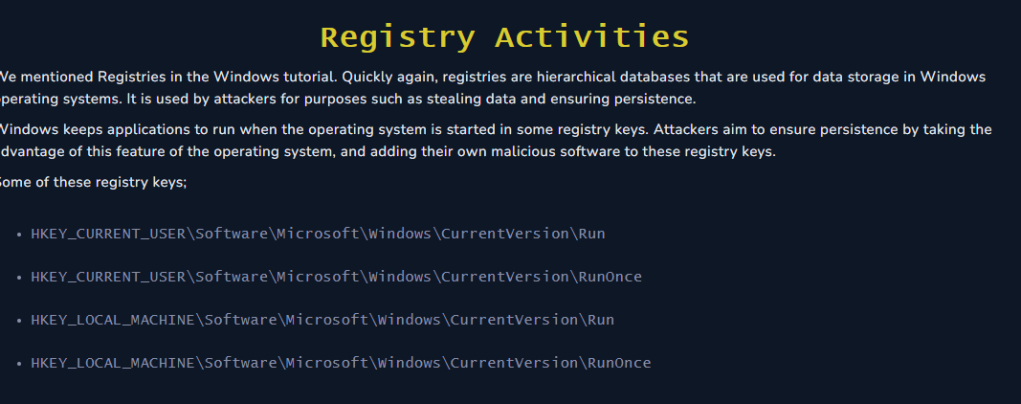
Let’s use the filter option again and search for these registries.