https://www.vulnhub.com/entry/rickdiculouslyeasy-1,207/
Review
- Explore the various ports to find flags
- FTP server can be accessed anonymously for a flag
- Web server enumeration will lead to a password and flag
- Use command injection to find users
- Access a user and examine other users files
- Transfer other user’s file to attacking machine to find for clues
- Create a password list with the clues given
- Check sudo permissions for privelidge exploitation
- Use Hacktricks for root access
Enumeration
Run nmap scan to find for open ports.



FTP Server
Able to access it annoymously.

Found a flag.

Port 9090

Unable to do much with he website as there is no login or password input.
Port 13337

Port 60000
Netcat into the port to find a flag

Port 80

Run a gobuster scan to find for hidden directories.

/robots.txt
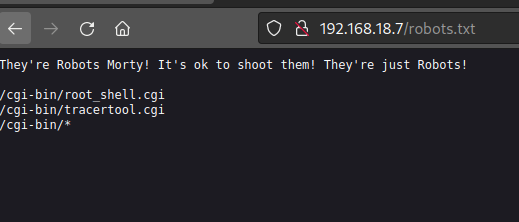


Let’s test for command injection.

Able to find a password list but when we cat we get a literal picture of a cat.

Tried to use alternatives like head and tail and no luck.

Use the tail command to check for users.

/passwords

Found a flag.

Found a password in the source code.


Foothold
Let’s try to ssh into the summer user with the password found.

Found a flag

Head to the Morty directory and there are two files. Let’s send this file over to the attacking machine to examine.

In the attacking machine , I use cat on the image to find a password.

Use that password to unzip the zipped file and you will get a cluse and a flag.

Head to RickSanchez folder and get the safe file into your attacking machine. Run the executable and use the previous flag number as an argument.

Cracking Rick’s password
I googled Rick’s band.

Now we need to generate a passwordlist that contains clues given to us.
Let’s use maskprocessor aka m64 to generate a wordlist



After some time I’m unable to get the password. I tried again with capital letters for the band’s name.

Cracked the password !

ssh into the new user

Check for sudo permissions

Privilege escalation

Root accessed gained.

Found a flag in the root folder

Flags Obtained
- FLAG{Whoa this is unexpected} – 10 Points
- FLAG{Yeah d- just don’t do it.} – 10 Points
- FLAG {There is no Zeus, in your face!} – 10 Points
- FLAG:{TheyFoundMyBackDoorMorty} – 10Points
- FLAG{Flip the pickle Morty!} – 10 Points
- FLAG{Get off the high road Summer!} – 10 Points
- FLAG: {131333} – 20 Points
- FLAG{And Awwwaaaaayyyy we Go!} – 20 Points
- FLAG: {Ionic Defibrillator} – 30 points