Network Enumeration
To begin our exploration of the network, let’s initiate an nmap scan in order to identify all open ports.

Web Enumeration
Run a gobuster scan to find for hidden directories.
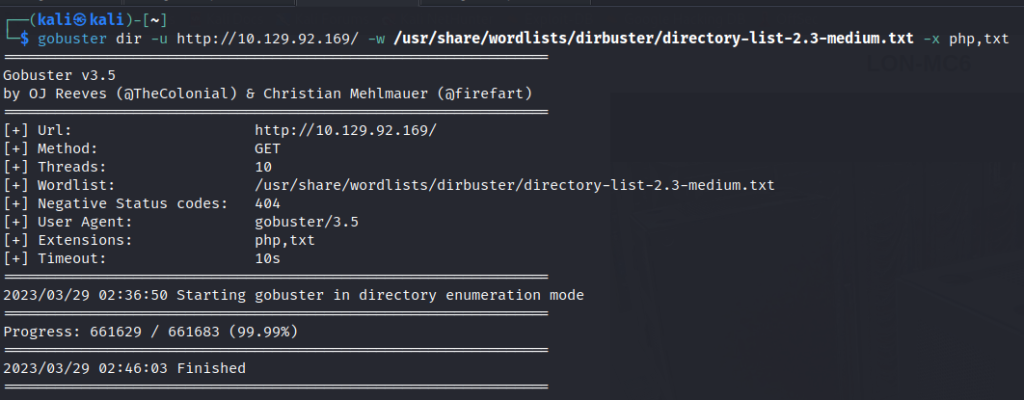
Unable to find any other directories.
Port 80

Website seems to be just an image.
FTP Enumeration
From the nmap scan we are able to gain access to FTP anonymously.

Head to the two folders and download the files in them.
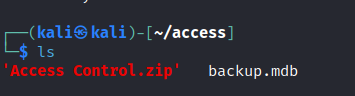
We get a zip folder that is password protected. I tired to bruteforce the password but it took too long.
The other file is a mdb file.
MDB file is a file format used by Microsoft Access to store data in a relational database. It’s used for organizing data into tables, forms, queries, and reports, and commonly used for inventory management, employee records, and financial data.
I use the strings command on the file and found a potential password for the Access file.

We get a .pst file.
A PST file is a personal storage table file used by Microsoft Outlook to store email messages, contacts, calendar appointments, and other items. It’s commonly used to archive or backup Outlook data, and can be opened and accessed on the same or different computer with Outlook installed.
Use the readpst tool to read the email. We get some creds.

Telnet
In our nmap scan the telnet post is open. Let’s use the creds to gain a shell.

Grab the user.txt in the desktop.

“cmdkey” is a command in Windows used to manage and manipulate stored usernames and passwords for accessing remote computers, servers, or resources. It allows users to view, add, or delete stored credentials, and can be useful for automating authentication processes.

The “runas” command in Windows allows a user to run a program as a different user or with different permissions than their current login. It’s commonly used for administrative tasks, such as installing software or accessing protected files.
Use the following command below to copy the root.txt file.
C:\Windows\System32\runas.exe /user:ACCESS\Administrator /savecred "C:\Windows\System32\cmd.exe /c TYPE C:\Users\Administrator\Desktop\root.txt > C:\Users\security\root.txt"We get the root.txt
