Category: Hacking
-

Attacktive Directory
99% of Corporate networks run off of AD. But can you exploit a vulnerable Domain Controller?
-
PNPT : Black Pearl
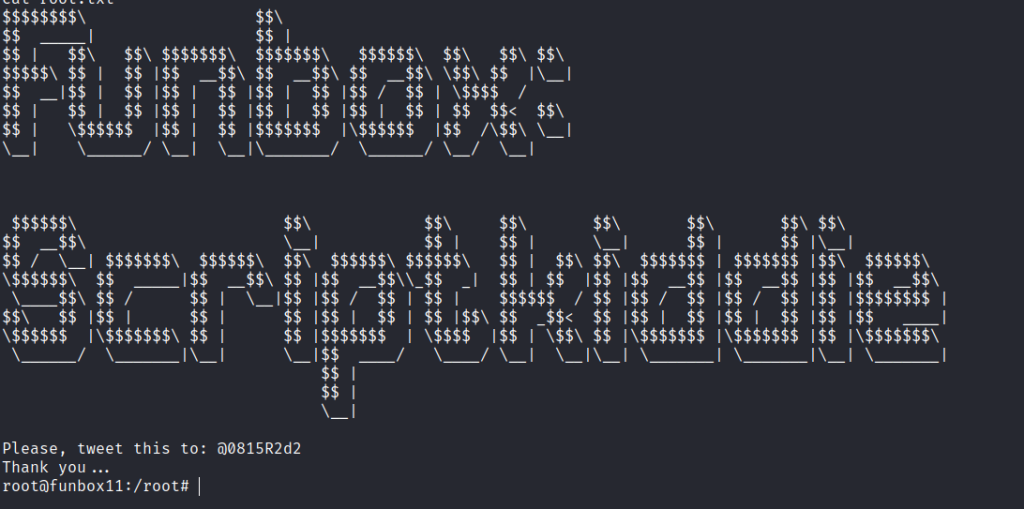
Overview Enumeration Run nmap scan to find for open ports. Run a gobuster scan to find for hidden directories. Port 80 /secret DNS Enumeration /navigate Foothold Use metasploit to gain a shell. Transfer linpeas to find more clues. Seems like we can exploit some permissions. Privilege escalation Check GTFObins for SUID exploits. Root is gained.
-
PNPT : Dev
Overview Enumeration Run nmap scan to find for open ports. Web enumeration Port 80: Run a gobuster scan to find for hidden directories. Port 8080: In the website at port 80 there is directory where we are able to find a config.yml file. This contains some creds that we can keep later. In the webserver…
-
PNPT : Academy
Overview Enumeration Run nmap scan to find for open ports. Run a gobuster scan to find for hidden directories. Port 80 FTP Enumeration Crack the hashed password Foothold Login to the academy page with the cred found and upload a reverse shell. View the config file to find creds for the administrator. Privilege escalation Edit…
-
Kioptrix 1
Overview Enumeration Run nmap scan to find for open ports. Port 80 & 443 Run a vulnerability scan with Nikto Start directory enumeration with dirbuster. SMB Enumeration Search for exploits Samba exploit https://www.rapid7.com/db/modules/exploit/linux/samba/trans2open/ Exploitation By metasploit Exploitation failed. Use a different payload. Root shell is gained. Exploitation by manual method
-

DC: 3.2
DC-3 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing. As with the previous DC releases, this one is designed with beginners in mind, although this time around, there is only one flag, one entry point and no clues at all.
-
Dina: 1.0.1
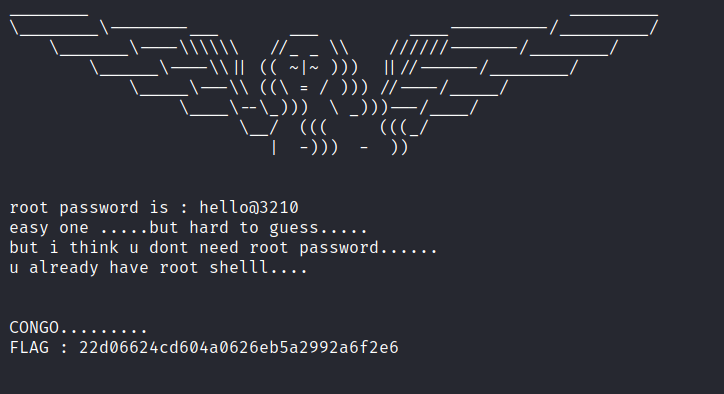
Download the machine: https://www.vulnhub.com/entry/dina-101,200/ Overview Enumeration Run nmap scan to find for open ports. Run a gobuster scan to find for hidden directories. Port 80 /robots.txt /nothing source code. /secure Unzip the file with the password list and a mp3 file is given. Use cyberchef to read the file. Now we found an interface. We…
-
Hacktoria : Intergalactic Warfare
Some clues we can get from the information given: The only “usual suspects” that I can think of is AREA 51. Let’s search for area 51 and look around the location. Found some cool planes. And even some choppers. Alright enough with sightseeing , we need to hunt for aliens. Just above AREA 51 we…
-

Hacktoria : Nightmare Fuel
Never thought I would say this but this is a creepy contract. Nevertheless it will be easy if you know the basis of steganography. I tried to find some clues in the video but it was dark and had no audio. I thought it could be a broken file. Tried to fix it online but…
-

Hacktoria : Prisoner of War
Read the description clearly to find some clues of the hidden location. We need to find the location of a nearby children’s hospital near the ambush area. Let’s start with searching for “Posté de contrôle KAYES” in google maps. Minimize the view and you can see a village near the ambushed area. We can see…
-
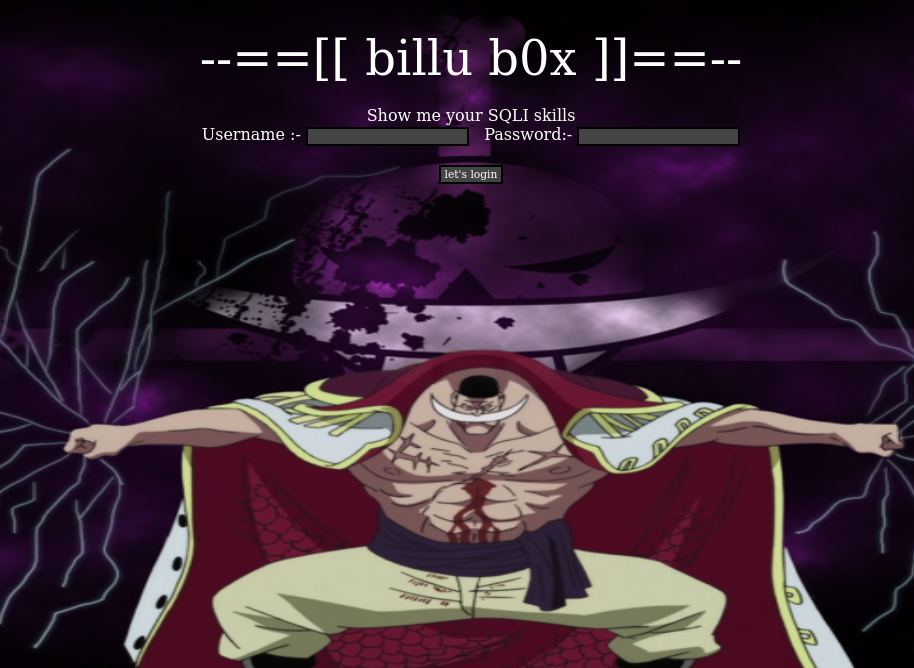
billu: b0x
This Virtual machine is using ubuntu (32 bit) Other packages used: – PHP Apache MySQL This virtual machine is having medium difficulty level with tricks. One need to break into VM using web application and from there escalate privileges to gain root access
-
Hacktoria : The Butcher
Contract : EASY Download the Password File which contains a HEX code. Head to Cyberchef which is a a web app for encryption, encoding, compression and data analysis. Paste the HEX code into the input. And choose the FROM HEX option in the Operations tab. It seems that the file is in another format. Let’s…
-
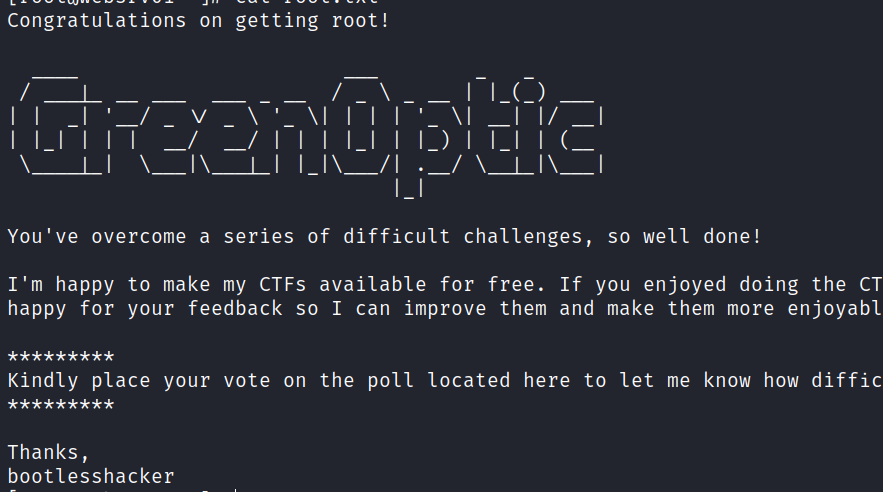
GreenOptic: 1
GreenOptic is my fourth Capture the Flag box. It is rated as ‘Very Hard’. As with all of my CTFs, please run this in ‘Host Only’ mode – it does not need an internet connection. Don’t let the difficulty put you off though – the CTF is designed to be realistic, so you won’t come…
-
476f64’s easyAF
https://crackmes.one/crackme/5eae2d6633c5d47611746500 Determine the file type Use the file command to determine the file type. Test the program Strings Use strings to print the sequences of printable characters in files. Analyze Dissemble the program in GDB Test the program